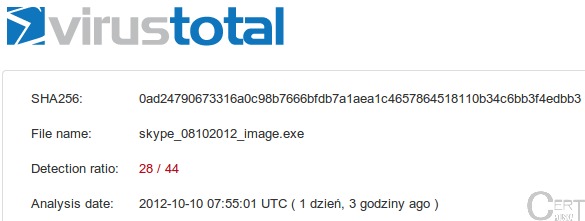
Recently there have been numerous reports about a new malware spreading through Skype. Since a couple of days, CERT Polska has also been taking an active role in disabling the Dorknet worm. A Polish security portal Niebezpiecznik.pl (article in Polish) mentioned that it also targets Polish users. We acquired a sample of this malware (called “Dorkbot”). This dropper was detected by 28 out of 44 antivirus used by the VirusTotal service:
Skype is not, in any sense, a new way of spreading malware. A couple of months ago we published an article about malware, known as “Pushbot”, that spread through Facebook, Skype and MSN. Pushbot was of course malicious, but, unless it downloaded additional malware, it “only” spammed our friends. Darkbot, on the other hand, has a very wide range of spreading capabilities and has several different malicious behaviors. As is stated in other news reports, it is most widely present on Skype. In order to infect users it sends a specific message in the user’s language containing a link to a dropper. Message in Polish reads:
http://goo.gl/f8p21?profile=TWOJA-NAZWA-SKYPE
This is not unlike Pushbot. It also spread through the use of a Google URL shortener. Also, the dropper file is hosted on
– the same service that was used by Pushbot to host additional malicious files that were run on infected machines.
What does it do?
When a user runs a file named (as our sample was)
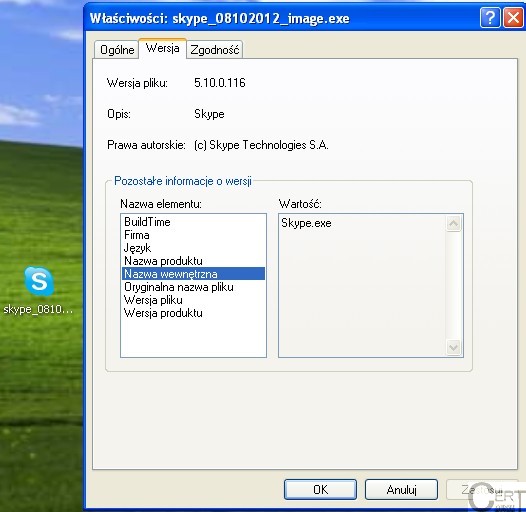
software unpacks itself and runs the “proper” Dorkbot. It is worth noting that all of the dropper details were crafted to pretend to actually be a Skype communicator (icons, details):
The unpacked Dorkbot takes only 94 kilobytes of disk space, but it contains a large variety of different functions. Just after being run, it checks whether it was initiated from the USB drive – if this is the case, it opens the USB drive in order to utilize the Windows autorun function. Next, it infects all processes that are present on the machine. By doing so, the malware ensures that it can create a naturally looking process tree. For example, when it infects
it also starts a child browser process –
(no matter what our default browser is) and communicates with the Internet through Internet Explorer. This process is created with a hidden window, which points to malicious behavior – the user does not know that data is sent to and received from the Internet. A firewall that only monitors unknown applications for its network activity would not suspect the browser application. This application is then used to communicate with the C&C server.
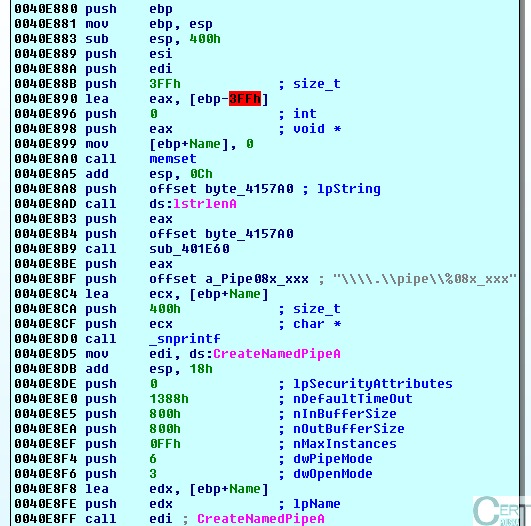
After infecting, the malware creates a named pipe (as we can see below), whose name starts with an eight digit hexadecimal number and ends with
. This pipe is used as a communication channel between all infected processes.
What are its capabilities?
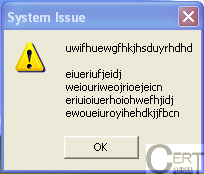
The alert window with gibberish presented at the top of the article is just a demonstration of one of Dorknet capabilities. Other than that, Dorkbot capabilities are quite impressive. Apart from the usual infections of USB drives or the downloading and running of additional software, it can also steal passwords from a vast number of services. These are mainly financial services, pornographic websites, hosting services or e-mail websites like:
youporn.com
brazzers.com
whmcs.com
webnames.ru
dotster.com
enom.com
1and1.com
moniker.com
namecheap.com
godaddy.com
alertpay.com
netflix.com
thepiratebay.org
torrentleech.org
vip-file.com
sms4file.com
letitbit.net
what.cd
oron.com
filesonic.com
speedyshare.com
uploaded.to
uploading.com
fileserv.com
hotfile.com
4shared.com
netload.in
freakshare.com
mediafire.com
sendspace.com
megaupload.com
depositfiles.com
eBay
officebanking.cl
twitter.com
secure.logmein.com
moneybookers.com
runescape.com
dyndns.com
no-ip.com
Steam
hackforums.*
Yahoo
Hotmail
Gmail
FastMail
BigString
AOL
Google / YouTube
PayPal
There is an interesting entry on the list – namely Megaupload. This website was closed at the beginning of this year, which probably means that Dorkbot was created before this time. It is also possible that this malware is able to extract passwords from the generic hosting panels, like e.g. cPanel. It also has the capability to spread through a number of communicators and social websites: Skype, MSN, Facebook, Bebo, Friendster, vkontakte and Twitter. As news reports state, Dorkbot downloads additional software and runs it on an infected machine – this file was, in the cases that we analyzed, hosted on hotfile.com – the same hosting that hosted Dorkbot dropper.
Apart from being overly social, Dorkbot has also some management capabilities. It can communicate over the IRC protocol with the cyber criminal and perform various commands. It can, for example, perform UDP flood attacks or attacks utilizing Ruskill or Slowloris.
We were unable to observe most of these behaviors in our laboratory, but there is code present to carry out these attacks. Below we present a part of the code responsible for conducting the UDP flood.
Polish ties
Dorkbot is also connected with the “Polish” Internet. As we mentioned at the beginning, Skype messages are also sent in the Polish language, which means that Polish users are one of the targets of the cyber criminals. However, we also observed that some of the C&C servers are present on Polish domains. Domains that are known to be connected with Dorkbot are:
dothome.pl
iziger.pl
How can you protect yourself?
Firstly, please do not click on any links that seem suspicious to you. Remember that even your friends can be infected and become a part of a botnet. You also should have an updated antivirus software and operating system.
Samples
The samples that we are analyzing was named
. In course of the analysis we were able to produce an additional two files. The first one is the unpacked Dorkbot (
) and the second one,
, was downloaded by Dorkbot. MD5 sums for these files are presented below.
67777ccbbb4dc60243cbb04a640741d2 unpacked.exe
30e594f768d7c2d4fca4546dd3c57f2e downloaded.exe
