
The project is a joint venture between NASK/CERT Polska (Poland) and National Cyber Security Centre (Netherlands). Goal of this system is to determine whether a site is malicious to the end-user. Scalability and ability to combine output from multiple client honeypots makes it an effective way of detecting malicious intents. One of the most important components of the system is a module that emulates web browser. Thanks to that module Honeyspider Network can classify not only a single website, but also a whole portal, by following the links from the main site. This a second, completely rebuild, edition of this project and for the first time its source code is available under the GPL license. All the necessary information can be found on www.honeyspider.net and on Cert Polska GitHub.
The major incentive to start this project is the rapidly growing number of browser exploits involving varying degrees of user interaction. Number of attacks against the client applications – web browsers, document readers or plugins that make it possible to display interactive content – is rapidly growing. Honeyspider Network tries to detect such threats by combining analysis results from different modules. It enables not only a detailed analysis of the threat, but also a detection of the threat source.
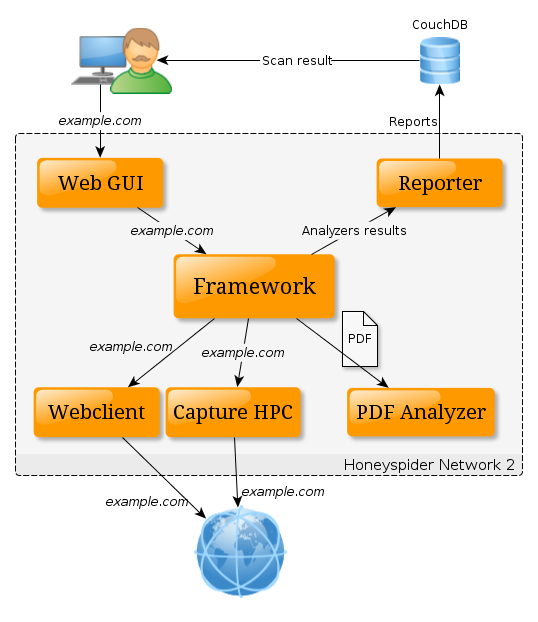
Main component of the system is the Framework, which facilitates the information exchange between different components. Honeyspider Network uses know, open source tools to store and process data, such as: HtmlUnit, RabbitMQ or CouchDB. Detection of the threats is based on, made especially for this system, JavaScript static analyzer, but also based on the output of the known threat detection tools like Thug, Capture-HPC NG or Cuckoo.
Whole system can be used directly from the web browser. This interface also provides support for multiple users with different permissions.
