At the start of October we started receiving reports of propagation of a new strain of unusual malware. This malware was dedicated for Polish online banking users and implemented a technique new to our market. We received a sample of this malicious software, written in Visual Basic 6. It used a fairly simple mechanism in order to steal money: whenever a user copied a text that contained a bank account number to the clipboard it switched that account number to a new one. This account was of course controlled by the cybercriminals.
Technical details
The user machine was infected through a phishing campaign, but we believe that this campaign was not a widespread one. Instead, it carefully crafted an e-mail content so that the victim would be persuaded to open the attachment. The infection vector was an attachment in the form of a zip archive containing a Windows screen saver file, which posed as a PDF document. This was achieved both by the file name (ending with
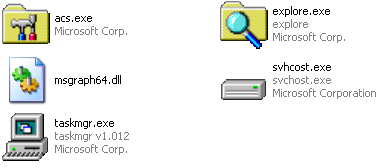
) and by the file icon, which resembled a standard PDF document icon. This dropper created files which were also created to resemble a benign Windows system file presented on the screenshot on the left.
In order to gain persistence on the victim’s system, the malware created a registry key under
. Additionally, the malware hides the file meant to be run on every windows boot by hooking WinAPI functions. This leads to a case where it is hard to find the file on the infected machine disk, despite the path to the file being clearly visible in the registry.
Inner workings
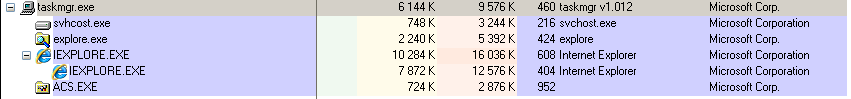
The malware, after creating all the files mentioned before, runs them in a specific sequence. Every executable file has its own purpose. The process tree related to the malicious software is presented above. The executable responsible for the C&C communication is
. It sends an e-mail (!!!), using SMTP protocol, to the attacker with a basic system info. It is also responsible for opening a website that has a statistics engine, which the attacker uses to track the number of infections.
Every time a user copies a 26 digit Bank Account Number, either as a one large number, or in the form of
it is replaced with a new number, hardcoded in the malware source code. The form of the number is preserved. Below is a screencast which presents this substitution process.
Every time we copy a number to Windows clipboard it is switched with another one, e.g. when we copy it from:
- a bill that we want to pay via wire transfer,
- an online auction website, when we want to pay for the goods we ordered,
- an e-mail messaged received from the online shop,
- an IM chat where our friend copied his account number and we want to transfer him money.
Summary
Despite the fact that the malware is very primitive in its construction, it uses an innovative way to fool a victim into transfering her money. This is why it is very important to check the account number before we confirm the wire transfer. CERT Polska was able to establish that this particular malware sample infected over 3000 machines. It was definitely targeting Polish users, as the Bank Account Number that was used as a replacement was created in one of the Polish banks. Below are all the MD5 hashes of the malware samples.
0af108f988b4d7ba00a041c4b5147d37 explore.exe
09ea238ec02f1c61b0af4d9596a0e90e svhcost.exe
c8efcb9657e1b16ba8a926558479e152 taskmgr.exe
303182dd4b3d32bc523153793e5d771f AcroRd.exe
