
The E-Security mobile malware appeared at the beginning of this year. This malware was targeting Polish online banking users, with the goal of stealing One Time Passwords (OTPs) used to confirm banking transactions. The attack was part of a bigger scheme. When the user computer was infected, it displayed an installation message when a user tried to log in to online banking website. This message instructed the user to install a mobile “certificate” app called “E-Security”. Recently this E-Security app was switched to a new one – more powerful and more dangerous, but essentially made for the same purpose – to steal OTPs sent via text messages to unknowing users.
Overview
The infection scheme is similar to the one described previously. A user upon logging in to the online banking website, is presented with a window that asks her to install a malicious application on her mobile phone. This time instead of a “security certificate” the request is to install a “mobile antivirus”. Text presented to the user is provided below (in Polish).
W związku z pojawiającymi się coraz częściej przypadkami instalacji niepożądanego oprogramowania na urządzenia mobilne, między innymi z Google play i App Store, nasz Bank wspólnie z liderem oprogramowania Antywirusowego opracował aplikację antywirusową dla urządzeń mobilnych. Nasz program antywirusowy uniemożliwia zainstalowanie podejrzanego oprogramowania, jak również usuwa wszystkie mobilne wirusy, które już są zainstalowane na Twoim telefonie.
W przypadku odmowy instalacji mobilnej aplikacji antywirusowej, bank NIE ODPOWIADA za zachowanie nienaruszalności środków finansowych na koncie klienta.
This can be translated to:
In the light of recent, more and more prevalent, mobile malware spreading through both Google play and App Store, our bank, working together with one of the leaders of the Antivirus software industry, prepared an mobile antivirus. This application prevents malware from installing and remove all mobile viruses that are already present on your phone.
Should you refuse to install this mobile application, the bank CANNOT BE HELD RESPONSIBLE for any malicious operation on the client bank account.
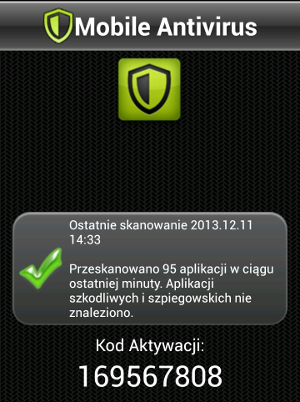
After user inputs her phone number, she receives a text message with a link to the malicious application. Then she is asked to provide an “activation code” on the website. This is to make sure that the user actually launched the application. The application is named “Mobile Antivirus” and its icon is presented at the beginning of this post. Application requires
ACCESS_WIFI_STATE
CHANGE_WIFI_STATE
READ_PHONE_STATE
CALL_PHONE
ACCESS_NETWORK_STATE
CHANGE_NETWORK_STATE
WRITE_EXTERNAL_STORAGE
ACCESS_NETWORK_STATE
INTERNET
RECEIVE_BOOT_COMPLETED
WRITE_SMS
READ_SMS
RECEIVE_SMS
SEND_SMS
RECEIVE_BOOT_COMPLETED
READ_CONTACTS
WRITE_CONTACTS
RECORD_AUDIO
ACCESS_FINE_LOCATION
MODIFY_AUDIO_SETTINGS
Additionally, after the installation, the user is required to add this application to the device managers. The device manager can request special kind of privileges – wider than are normally permitted. This application requests a privilege to wipe all user data and control screen lock. The message that is displayed is presented on the left. The text that justifies this kind of privileges is also worth noting: “Additional text explaining why this needs to be added.”
Other graphic templates
This application not only poses as a mobile antivirus – it can also imitate a mobile banking application of a specific bank. However, we observed only such cases for non-Polish banks. This targeted version asks user for some kind of password and only then provides her with an “activation code” – in a similar manner as in the more generic version.
The application is designed in such a way that it is very easy to switch between different UIs. The Figure on the right presents a generic, Polish, application interface with a text that is provided at the end of “antivirus scanning”.
Botmaster authentication
As in the E-security case, HTTP is not the only channel that botmaster can use in order to issue commands. Text messages are also used for this purpose. Commands can be sent either from the hardcoded phone number or after an authentication of the new number. This authentication is performed by sending a text message containing password to the bot phone number. After this operation, the botmaster can control the phone by sending subsequent messages from the same number. In this case a number of available commands is impressive.
This malware can, for example:
- Send information about the phone state (Internet connection state, manufacturer name),
- record sounds using built-in microphone,
- get image files from an SD card (file with
<span class="text">jpg, jpeg, gif, png</span>
extensions),
- get all messages in the SMS inbox,
- get a list of all installed apps,
- delete all of the user data,
- record phone calls,
- localize user based on the GPS or cell network information,
- get a contact list,
- redirect phone calls by using the
<span class="text">*21*phone_number#</span>
USSD code,
- send text messages to any number,
- save all text messages in order to pass them to the attackers.
Technical details
The malicious app adds a
receiver, i.e. the class that handles the event of phone boot. After receiving such an event, the app starts two services:
and
. The former is responsible for establishing the SMS communication channel, while the latter is responsible for establishing the HTTP connection. Both the application settings and the data it extracts (e.g. text messages) are saved in the SQLite database named
. The activation code is generated randomly. HTTP communication is encrypted using
cipher in the
mode. This is implemented using calls to standard Java cryptography API:
.
Summary
Polish online banking users are gradually becoming a more popular target for mobile malware creators. These attackers use different kinds of malware for the same purpose: to obtain an unrestricted access to victim bank accounts by subverting OTP mechanisms used to confirm transactions. Additionally, this particular malware can wipe user data in order to make the forensic analysis harder for the researchers.
Below is the SHA-256 sum of the sample that we analyzed.
