In the last two weeks, the CERT team received multiple reports describing suspicious e-mail messages supposedly coming from the Warszawa Wola (a Warsaw district) Bailiff office. The message contents do not describe the alleged due in detail, thus encouraging the recipient of the message to click on the link described as “Payment Order Photocopy”.
In the messages that we received, clicking the link that leads to the alleged payment order results in the download of an executable file (dropper) disguised as a PDF. After the user clicks on the PDF document, the JPEG image of the “document” is unpacked, along with the malware, that is then deployed to the system.
The “document” is then displayed using Windows Image Viewer launched by rundll.
The malware
The malware deployed by the dropper is a simple commercial spyware called Ardamax Keylogger. It allows keyboard snooping and monitoring following online communicators: AIM, Windows Live Messenger, ICQ, Skype, Yahoo Messenger, Google Talk, Miranda, and QiP. Ardamax Keylogger also has the option to make periodical screenshots, snapshots of computer’s environment using connected or built-in camera, and clipboard contents interception. The exfiltration of the collected data is done using e-mails, FTP or by saving to a predefined Windows network share. After it is installed, the attacker has no way to change its settings, there is no C&C nor any bidirectional communication with the spyware besides collecting its logs.
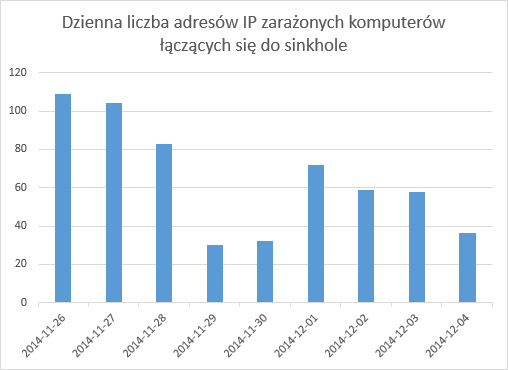
The objectives of the campaign are unclear. We are now proceeding with mitigation of the campaign. We have taken over fourteen domains used for dropzones and redirected them to our sinkhole, and two more domains were disabled. If your Windows PC periodically connects to 148.81.111.108, this means that you are a victim of this spyware campaign. The following chart shows number of infected addresses connecting to our sinkhole:
Below attached is formal indicators of compromise list in Mandiant IOC format and MD5 hashes:
- IoC: ekomornik.zip
- MD5 / VirusTotal Score:


