
Zaufana Trzecia Strona – a Polish security news portal – informed about a new attack on Polish user’s (link is in Polish) that used a Microsoft Office plugin install wizard as a decoy. In reality, the user not only installed the plugin, but also a malware called Smoke Loader. It allows the attacker to gather information about the infected machine and, among other things, redirect its DNS queries. We wrote an article about that malware, when we were informing about the infected sites in the gov.pl domain. Here we describe some features of Smoke Loader that seem new to us.
Campaign
ZaufanaTrzeciaStrona.pl provided us with samples for this analysis. The attack vector is described in details in the article at z3s.pl (in Polish). To give the background for an English-speaking audience, what follows is a description of the attack. A user received an e-mail message asking him to look at some documents. The message was prepared taking into account the user’s job position and was written in perfect Polish. If a user clicked on a link, she was redirected to a website which asked to install Microsoft Office plugin for her web browser in order to display the document. The user then downloaded the installer for this plugin. This installer was bundled with another app, DONEAPP.EXE, which was run during the installation process and contained a malware called Smoke Loader. Below is a screen from an installation process.
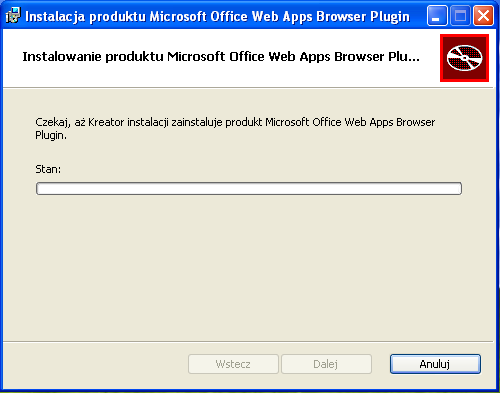
Smoke Loader – network traffic and installation
DONEAPP.EXE is a packer in Visual Basic, which unpacks and runs Smoke Loader malware. This malware gains persistence on the users server by adding an appropriate registry autorun key. It also copies itself to an %APPDATA% directory with a random name. The executable file has the same name as the directory.
Smoke Loader test Internet connection by sending a GET request to one of the URLs in the msn.com domain and hides C&C traffic by doing some POST requests to URLs found in the Windows Registry – usually taken from installed software. A sample of this traffic is shown below. This kind of footprint can be used for an early detection of Smoke Loader in your network.
Then, if the connection test is passed, Smoke Loader contacts the C&C server cannedgood.eu, which disposes the tasks. This communication is encrypted. The C&C infrastructure is now abandoned, because of the publicity regarding the attack.

Smoke Loader – new plugins
The Smoke Loader used in this campaign contained plugins called Rootkit.dll and Faker.dll, which hooked WinAPI in order to hide malware activities or capture and change the DNS requests and responses. The screenshot below shows that first bytes of NtEnumerateValueKey were changed and now contain a jmp instruction to a code located in the Rootkit.dll library. This is done in order to hide the aforementioned autorun key from any applications that want to access Windows registry.
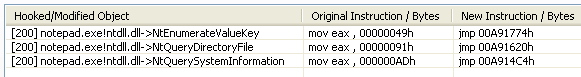
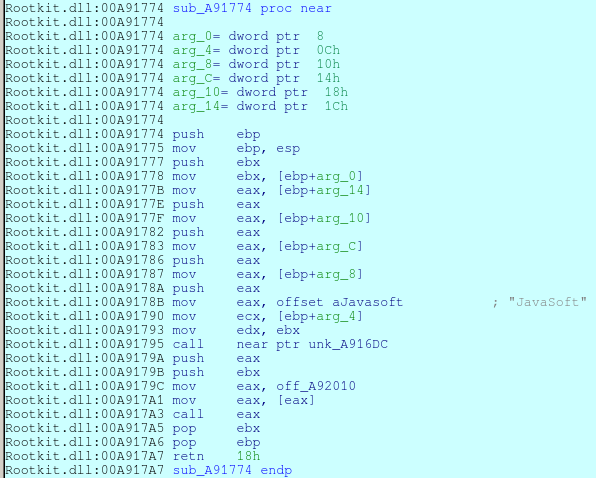
NtEnumerateValueKey is run, Smoke Loader checks whether the process asked for a value of JavaSoft key. If it did, then this key is hidden from the result of the function call. This is the name of the key which holds a path to Smoke Loader and is responsible for its autorun.
NtQueryDirectoryFile – function responsible for providing a listing of file in a specified directory. This hides the executable file containing the Smoke Loader.
During our analysis, Smoke Loader downloaded another plugin called Faker.dll. The purpose of this plugin is to intercept all DNS queries and, in some cases, return different IP address. This can be useful for example in phishing attacks. Unfortunately, we were not able to identify affected domains.
Summary
It is not that often that we see such a professional malware campaign specifically directed at Polish users. Info about samples and some behavioral analysis can be found on the z3s.pl site and additional technical descriptions of the Smoke Loader can be found under the following URLs:
- http://stopmalvertising.com/rootkits/analysis-of-smoke-loader.html
- http://eternal-todo.com/blog/smokeloader-analysis-yulia-photo
