Publication of our annual report is coming soon. Editing is moving forward at full speed, but in the meantime we’d like to share some statistics concerning 2018. This statistics provide a big bicture of an IT security landscape in Poland and as well conclusions about major trends in this area. For many years already CERT Polska has incorporated eCSIRT.net incident classification (now, the sixth version marked as mkVI)1, which defines pretty well different incident categories.
In 2018 operators of CERT Polska received 19439 incident reports. We carefully analyzed and categorized all of them. Among these reports, 5675 were the reason to register incident. Our team created 3739 security incidents, what gives on the average over 10 incidents created daily. The remaining a dozen or so reports not assigned to any incident were irrelevant or can be considered as automatic alerts sent from several alerting systems. In case of the latter our activities were connected with supplying our n6 platform2 and other analytic tools as well.
Often, one incident can be connected with many incident reports, e.g. three different entities report the same phishing site.
In the table below we present incidents handled by our team, divided into categories according to eCSIRT.net classification.
| Category | Incidents | % |
|---|---|---|
| Abusive Content | 431 | 11,53 |
| Spam | 419 | 11,21 |
| Harmful Speech | 5 | 0,13 |
| Child/Sexual/Violence/… | 0 | 0 |
| Unclassified | 7 | 0,19 |
| Malicious Code | 862 | 23,05 |
| Virus | 4 | 0,11 |
| Worm | 0 | 0 |
| Trojan | 117 | 3,13 |
| Spyware | 0 | 0 |
| Dialer | 1 | 0,03 |
| Rootkit | 1 | 0,03 |
| Unclassified | 739 | 19,76 |
| Information Gathering | 101 | 2,7 |
| Scanning | 80 | 2,14 |
| Sniffing | 1 | 0,03 |
| Social Engineering | 7 | 0,19 |
| Unclassified | 13 | 0,35 |
| Intrusion Attempts | 153 | 4,09 |
| Exploiting of known Vulnerabilities | 30 | 0,8 |
| Login attempts | 37 | 0,99 |
| New attack signature | 0 | 0 |
| Unclassified | 86 | 2,3 |
| Intrusions | 125 | 3,34 |
| Privileged Account Compromise | 11 | 0,29 |
| Unprivileged Account Compromise | 21 | 0,56 |
| Application Compromise | 35 | 0,94 |
| Bot | 4 | 0,11 |
| Unclassified | 54 | 1,44 |
| Availability | 49 | 1,31 |
| DoS | 7 | 0,19 |
| DDoS | 35 | 0,94 |
| Sabotage | 0 | 0 |
| Outage (no malice) | 1 | 0,03 |
| Unclassified | 6 | 0,16 |
| Information Content Security | 46 | 1,23 |
| Unauthorised access to information | 21 | 0,56 |
| Unauthorised modification of information | 13 | 0,35 |
| Unclassified | 12 | 0,32 |
| Fraud | 1878 | 50,23 |
| Unauthorized use of resources | 1 | 0,03 |
| Copyright | 8 | 0,21 |
| Masquerade | 43 | 1,15 |
| Phishing | 1655 | 44,26 |
| Unclassified | 171 | 4,57 |
| Vulnerable | 69 | 1,85 |
| Open for abuse | 14 | 0,37 |
| Unclassified | 55 | 1,47 |
| Other | 25 | 0,67 |
Table 1. Incidents handled by CERT Polska, divided into eCSIRT.net categories
In 2018 CERT Polska created 17,5% more incidents comparing to 2017. Most of them were categorized as phishing, malware or spam. According to the data from 2017 we observed slight change on the podium in that infamous ranking, because then the first three places went as follows: phishing, malware, intrusions. Proportion of phishing incidents remained on similar level comparing to 2017 and reached 44%, which was firmly dominant result above remaining categories. Most popular scenarios were connected with phishings on foreign servers targeting Polish financial institutions (mostly banks). Another popular scenarios were related to phishings targeting services like Netflix or PayPal served from compromised Polish servers. Leading theme behind those attacks was premium users’ credentials theft or simply stealing money from internet bank account. Many scenarios concerned also selling goods on advertisement websites at the attractive prices. Main objective of these operations was to persuade users to enter sensitive data on fake websites, impersonating online payment platforms like Dotpay or PayU.

Website impersonating online payment platform
In 2018 we also observed fake online shops business, which has been visibly developed by some actors. In last year number of incidents related to fake online shops tripled, comparing to 2017. At this point, we’d like to thank all users aware of this kind of threat, who report about such activities more often and more eagerly every year. Attackers tried to find as many victims as possible, e.g. by advertising their shops in social media and popular search engines, where they were optimizing their shops’ position on the list of search results.

An example of a fake shop “offering” electronics at the attractive prices
The second most popular category of incidents was malware. It’s a broad category with many subcategories, but usually we marked incidents related to malware as “unclassified”. Firstly, because in many scenarios more than one malware family was used, incorporating variety of methods and attack techniques. Secondly, we registered significant number of incidents concerning ransomware, which unfortunately don’t have its own category in eCSIRT.net classification. In that aspect the classification isn’t perfect yet, but we hope that in the next revision it will be updated.
A vast number of malware incident reports was related to attacks on Polish users. Popular scenarios concerning emails with fake invoice, delivery details or claim for payment (or additional payment) continued spreading in different versions. These emails usually contained malicious attachment as a script, document with macros or link leading to some website distributing malware (e.g. banker or mobile banker app, depending on User-Agent HTTP header).
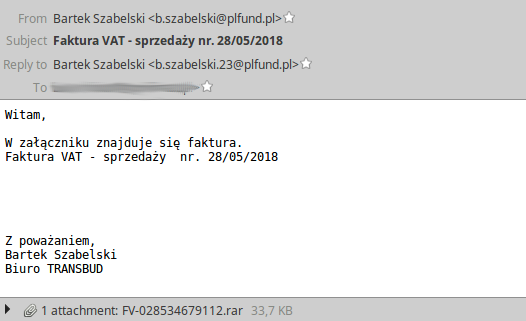
Email with malicious attachment pretending to be an invoice
This year for the first time we publish classification of incidents divided into Polish economy sectors. You can find detailed information in the table below. At a glance significant number of incidents is marked as Other (3 out of 4 incidents were classified to this category). These were mostly incidents concerning individuals or private entities. Next places in the classification belong to banking sector and public administration. Total number of the latter was little, comparing to the Other category. We are aware that presented classification is far from ideal. However, we had created this classification before CERT Polska has been designated as one of the three national-level CSIRTs under National Cybersecurity System law. Now, when the law is in force, we’ll be able to specify categories of this classification to reflect security of different economy sectors in a better way.
| Sector | Incidents | % |
|---|---|---|
| IT infrastructure | 29 | 0,78 |
| Public health care | 13 | 0,35 |
| Banking | 643 | 17,2 |
| Other financial institutions | 62 | 1,66 |
| Energy industry | 20 | 0,53 |
| Transport | 51 | 1,36 |
| Public administration | 85 | 2,27 |
| Water supply | 2 | 0,05 |
| Other | 2834 | 75,8 |
| Total | 3739 | 100 |
Table 2. Incidents handled by CERT Polska divided into Polish economy sectors
More conclusions you’ll find in our annual report (coming soon). You’re warmly welcomed to follow CERT Polska’s blog and our profiles in social media to be up-to-date with latest news concerning publication of our report.
