We are happy to announce that we are releasing a free decryption tool for the Mapo (a GarrantyDecrypt/Outsider variant) ransomware today. We would also like to thank Maciej Kotowicz of Kaspersky’s GReAT for sharing his insights on the ransomware’s encryption process.
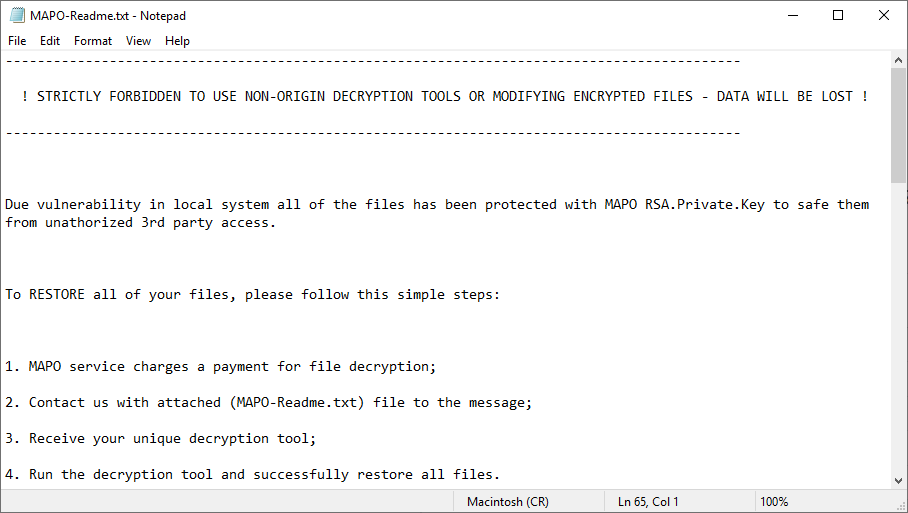
Our tool works with encrypted files having the .mapo extension and the following ransom note attached as “MAPO-Readme.txt” file:
The tool is no longer publicly available, but feel free to contact us if you still need it.
