We proudly announce that today we open-source a large part of our analysis framework and pipeline!
If you want to try it – check out Karton project on GitHub.
What is karton?
Karton is a robust framework for lightweight and flexible analysis backends. It can be used to connect malware analysis systems into a robust pipeline with very little effort.
We’re in the automation business since a long time. We’re dealing with more and more threats, and we have to automate everything to keep up with incidents. Because of this, we often end up with many scripts stuck together with duct tape and WD-40. These scripts are written by analysts in the heat of the moment, fragile and ugly – but they work, and produce intel that must be stored, processed further, sent to other systems or shared with other organisations.
We needed a way to take our PoC scripts and easily insert them into our analysis pipeline. We also wanted to monitor their execution, centralise logging, improve robustness, reduce development inertia… For this exact purpose, we created Karton.
Projects to check out
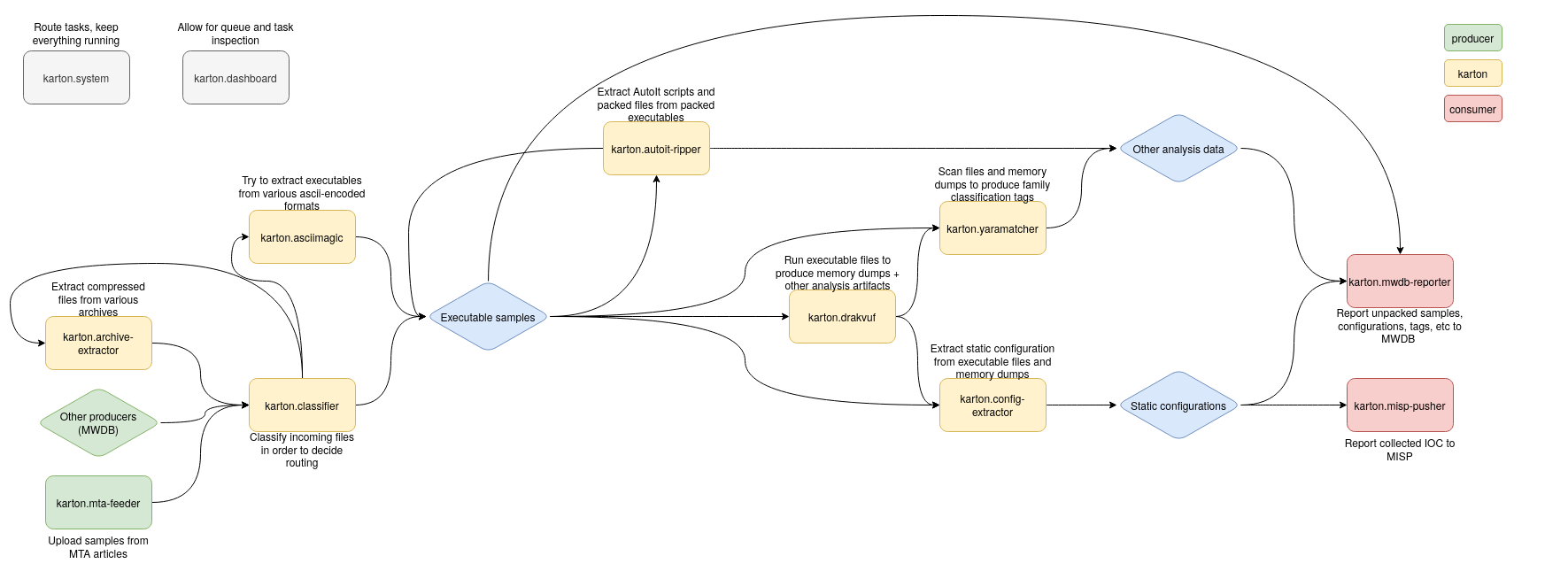
This is not a single system, but rather a collection of microservices. There are many small utilities, that may not be groundbreaking on their own, but compose nicely. They include:
- karton – The main repository. It contains the karton.system service – main service, responsible for dispatching tasks within the system. It also contains the karton.core module, that is used as a library by other systems.
- karton-dashboard – A small Flask dashboard for task and queue management and monitoring.
- karton-classifier – The “router”. It recognises samples/files and produces various task types depending on the file format. Thanks to this, other systems may only listen for tasks with a specific format (for example, only zip archives).
- karton-archive-extractor – Generic archive unpacker. Archives uploaded into the system will be extracted, and every file will be processed individually.
- karton-config-extractor – Malware extractor. It uses Yara rules and Python modules to extract static configuration from malware samples and analyses. It’s a fishing rod, not a fish – we don’t share the modules themselves. But it’s easy to write your own!
- karton-mwdb-reporter – A very important part of the pipeline. Reporter submits all files, tags, comments and other intel produced during the analysis to MWDB. If you don’t use MWDB yet or just prefer other backends, it’s easy to write your own reporter.
- karton-yaramatcher – Automatically runs Yara rules on all files in the pipeline, and tags samples appropriately. Rules not included ;).
- karton-asciimagic – Karton system that decodes files encoded with common methods, like hex, base64, etc. (You wouldn’t believe how common it is).
- karton-autoit-ripper – A small wrapper around AutoIt-Ripper that extracts embedded AutoIt scripts and resources from compiled AutoIt executables.
- karton-drakvuf (coming soon) – Uploads incoming samples to drakvuf-sandbox for dynamic analysis.
- karton-misp-pusher (coming soon) – A reporter, that submits observed events to MISP.