-
CFP Secure 2020

24th edition of iconic and the oldest cybersecurity conference in Poland. Do you love being on stage (or at least you don’t faint) and have something interesting to say? Apply! Why SECURE? There are many cybersecurity teams in Poland, but there is only one CERT Polska. And it guarantees …
Read more -
Strengthening our malware analysis capabilities

During last year we have collaborated with Hatching.io on improving the open source Cuckoo Sandbox. The main works were focused on porting advanced mechanisms for memory analysis which were developed internally by our team in the previous years. The public release of the onemon marks the last stage of …
Read more -
SECURE 2018 – Call for Speakers

Call for Speakers for SECURE 2018 is now open. If you have an interesting topic and would like to share your ideas with a crowd of Polish and international IT security specialists, please consider submitting your proposal. You will find all applicable information below. SECURE 2018 will be held on …
Read more -
We are joining the No More Ransom Project

From the beginning of April we are officially an Associate Partner of the No More Ransom Project. Its main goal is to fight ransomware by helping victims with free decryption of their files. It is coordinated, among others, by Europol, and it connects law enforcement agencies and private sector companies …
Read more -
Network traffic periodicity analysis of dark address space
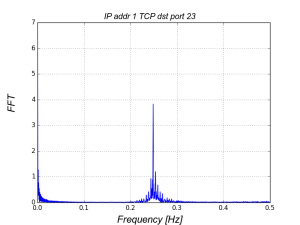
Network traffic directed to dark address space of IPv4 protocol can be a good source of information about current state of the Internet. Despite the fact that no packets should be sent to such addresses, in practice various traffic types can be observed there, for example echoes of Denial of …
Read more -
01 October 2015 piotrb #botnet #detection #detection system #detekcja #dga #DNS #NXDomain #system detekcji
How non-existent domain names can unveil DGA botnets

Domain Generation Algorithms are used in botnets to make it harder to block connections to Command & Control servers and to make it difficult to takeover botnet infrastructure. The main objective of these algorithms is to generate a big number of different domain names which usually look random, like Read more