
Our annual report for 2010 presents and comments on statistical data derived from CERT Polska daily operations in 2010. The outcome is a comprehensive analysis of network threats affecting Polish networks as we see them. Unlike previous years, when we focused on manually handled incidents, the data presented in the current report is collected largely in an automated fashion from various external and internal systems, yielding millions of records. This allowed us to produce a report analyzing over 12 million submissions that we consider a unique and fairly authoritative picture, not only due to amount and variety of data, but also the extent in which Polish networks are covered.
We have taken a more detailed look at some categories of data, such as
- “traditional” phishing pages,
- malicious webpages,
- spam,
- scanning,
- bots.
- Poland does well in comparison to other countries of similar size and IT usage levels in terms of number of threats originating in the networks of a given country. Poland is behind the top 10 “attacking” countries in all statistics we are aware of.
- In regards to spam, Poland has dropped from the top 10 lists for the first time in many years. This is mainly thanks to filtering of port 25/TCP introduced by Polish Telecom. Similar actions of other ISPs would certainly help to mitigate spam even more.
- Large majority of web based threats originating in Poland, including phishing and malware injections are placed at services run by hosting providers.
- At least 9 percent of Polish websites where phishing cases were observed belonged to legitimate e-commerce sites.
- Networks of mobile operators are clearly emerging sources of scanning and spam.
- Overwhelming majority of scans hits port 445/TCP, which can mostly be attributed to Conficker activity. It is quite likely that this worm was responsible for most of the infections among Polish internet users.
- Attacks on Voice-over-IP services are becoming a serious threat. They can be observed both as scanning activity and real cases of successful attacks, usually resulting in serious financial losses.
- The amount of spam, both worldwide and observed in Poland is not rising. In the second half of 2010 a decreasing trend was clearly visible.
- The service which attracted the largest share of interest among Zeus miscreant users was PayPal. Polish banks most often appearing in Zeus configuration files: ipko.pl and bsk.com.pl.
- Polish file storage and sharing service like wrzuta.pl and przeklej.pl are being used for distribution of malicious software.
- DDoS attacks, although relatively rarely reported, are having harmful effects. We have noted cases of such attacks that involved a blackmail attempt.
- In 2010 we have witnessed the first real threat to industrial systems – the Stuxnet worm.
- Drive-by downloads remain among the most common ways to infect end users’ systems. It involves placing a piece of malicious code inside a web page in order to exploit a vulnerability in a browser or one of it’s plugins in an automated manner, without additional interaction with the user.
The chart below shows numbers of events in all categories (note the logarithmic scale):
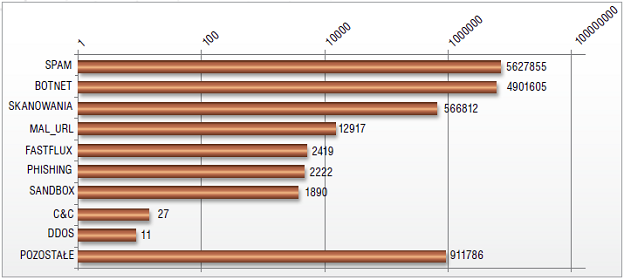
We also present data from our incident response system, and compare it to numbers from previous years, identifying trends.
The report has sections dedicated to what we view as last year’s most prominent Internet security “phenomena”, such as the proliferation of the Zeus trojan, Stuxnet or the rise of Voice-over-IP attacks. We also include a report from the ARAKIS early warning system. The latter includes descriptions of attacks on Facebook and proFTPd daemon, based on observations from our honeypots.
Below are the most interesting findings based on the report:
The report (in Polish) can be downloaded from: http://www.cert.pl/PDF/Raport_CP_2010.pdf
