
Recently, we obtained a new Android malware sample, which is targeting Polish e-banking users. The application is called “E-Security” and its filename is
. It also has a security-related icon shown on the left. The malware is relatively simple, but effective at achieving its goals. It allows an attacker to redirect text messages containing one-time passwords from the victim’s phone. The application itself consists of only one screen informing users (in Polish) that the level of e-banking security has been heightened and certain actions are required …
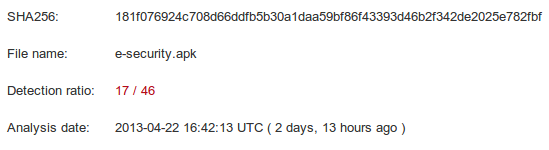
Screenshot above presents VirusTotal analysis results of the sample.
E-Security AES256 Certificate installation
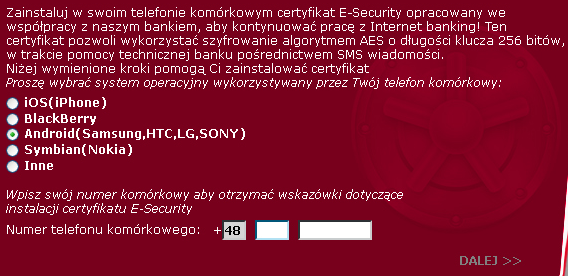
Installation of this malware is performed in multiple stages. Firstly, a victim’s machine becomes infected. After that a notice is displayed when the user visits their e-banking transaction system. It is made in such a way that suggests that this message comes from the bank website. It informs a user that she should install a “E-Security certificate” that will “enable you to encrypt communication using AES cipher with a 256 bits long key”. This notice is displayed using a man in the browser attack that was described in details in our most recent botnet takedown report. In order to download this “certificate” the user must enter her phone number and choose a mobile operating system that her smartphone is running. An example of such a notice is shown below.
After user provides that information, she receives a text message, persumably from the bank itself, with the URL address to the apk file. Attackers even explain to the user how to turn on installation of the app from unknown sources (outside the official marketplace). This setting, they claim, is necessary, because the app is a “proprietary bank software, which may cause your smartphone to reject it’s installation”.
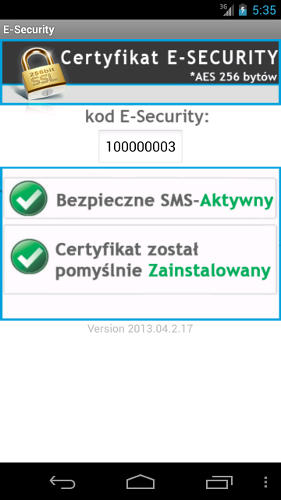
After the installation, the user is asked to provide her “E-Security code”. This code is displayed after running the application and is based on the phone’s IMEI number. Screenshot from the app is shown on the right. By forcing the users to do this, attackers make sure that the user has ran the application and are able to connect phone’s IMEI number with user login and password. The app screen is written in Polish, which clearly means that Polish users are the primary target.
Inner working of the E-Security AES256 encryption
The application requests all of the permissions available for Android phones. This may be in order to obfuscate it’s actions and hide the real purpose. Most important parts of the
file are shown below.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 | <table cellspacing="0" cellpadding="0"> <tbody> <tr> <td class="line-numbers"> <div>1 2 3 4 5 6 7 8</div></td> <td> <div class="text codecolorer"><service android:name=".SecurityService" android:enabled="true" /> <receiver android:name=".SecurityReceiver"> <intent-filter android:priority="2147483647"> <action android:name="android.provider.Telephony.SMS_RECEIVED" /> <action android:name="android.intent.action.NEW_OUTGOING_CALL" /> <action android:name="android.intent.action.BOOT_COMPLETED" /> </intent-filter> </receiver></div></td> </tr> </tbody> </table> |
These entries describe the actions taken by the malware. First a Service called
and a Receiver called
are installed. The receiver is meant to be fired whenever the phone receives a text message, the user makes an outgoing call or the smartphone boot sequence is completed.
However this receiver only makes use of the received SMS. This malware is controlled by text messages and it only has four commands. Messages sent from the C&C are always invisible to the phone user.
„Get Info” command
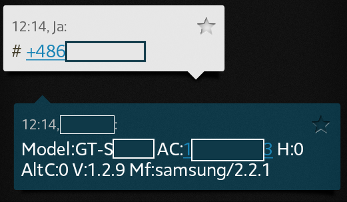
First type of command is „Get Info”. In order to issue this command C&C must send a text message that starts with a hash sign and has a phone number somewhere in the text. This phone number must start with the plus sign. In response to this message malware sends the following text message to the number provided in the message body (message origin is completely ignored):
1 | Model: AC: H: AltC: V: Mf:/ |
In this message
means the phone model,
is the IMEI-based unique identifier,
specifies whether the malware actions are hidden,
specifies whether text messages are being forwarded or not,
is the malware version (in our case 1.2.9),
is the phone’s brand name and
is the Android OS version.

“New Number” command
When the malware receives a text message that starts with a slash and has a phone number in it’s content, it assumes it received a “new number” message. From now on, all of the text messages will be redirected to that number. This allows the attackers to forward all of the one-time passwords sent from the victim’s bank. Now, the attacker is able to perform a wire transfer to the account he controls. It is worth noting that messages can be forwarded to the different number that the origin of the control command text message. This allows the attacker to hide her actions even more efficiently.
“Fin” command
When the infected phone receives a message that starts with a comma, it assumes that this is a “fin” message. This message must be sent from a number to which the text messages were being forwarded. This command ends forwarding and makes the malware wait for another control command. When the attacker turns on message forwarding for a small amount of time, it may even be possible that user will be unaware that her text messages are redirected somewhere else.
“Uninstall” command
Every text message that starts with the exclamation mark (!) is assumed to be the “uninstall” command. This command removes the malware from the infected phone. This is the last command that the attacker can send, i.e. it is irreversible.
Detailed logging and additional functionalities
This malicious app, apart from being able to receive commands from the text messages, also has a functionality to report text messages to a specified URL address. In the sample that we received this functionality was turned off and was not completely implemented. We were able to determine that, in another scenario, the app would send the text messages inbox contents to the specified URL address. This address was hardcoded in an obfuscated manner to make it harder to find by regular expression matching. Unfortunately, our sample had an empty URL address, but the deofuscating code is presented below.

This malware makes an extensive use of the logging mechanisms. Below is the example of log file generated by this application in our testing environment. This snippet was produced after issuing the “get info” command on the infected phone.
is used by the developers to specify that the app is controlled by text messages (as opposed to reporting via HTTP).
1 2 3 4 | I/SSuite ( 1904): AlternativeControl called I/SSuite ( 1904): AlternativeControl control message GET INFO I/SSuite ( 1904): SendControlInformation called number is +486xxxxxxxx I/SSuite ( 1904): Model:GT-Sxxxx AC:1xxxxxxx3 H:0 AltC:0 V:1.2.9 Mf:samsung/2.2.1 |
Sample information
The sample that we obtained was named
and its SHA-1 and MD5 hashes are presented below.
1 2 | e55c3a9586a858ee931c21ec7cae90276e7ddc16 02462f235a01a6f8287900d04598b4a4 |
