![]()
In our previous article we described a new VB malware, named VBKlip by us, that was replacing a Bank Account Number that was copied to the Windows clipboard. In order to check whether your computer is infected you have to just simply copy a correct Bank Account Number (e.g.
) and paste it into the text editor (e.g. Microsoft Word or Notepad) and compare the pasted number with the copied one. If they are different then your machine is most probably infected with the described malware strain.
How to remove malware?
In order to remove this malware we will use the previously described technique. Firstly, we will need to download and unpack SysInternals Autoruns (available at http://technet.microsoft.com/en-us/sysinternals/bb963902.aspx). This archive should contain four files:
|
1
2 3 4 |
Autoruns.chm
Autoruns.exe Autorunsc.exe Eula.txt |
Upon running the
we should see the main autoruns window, as pictured below:
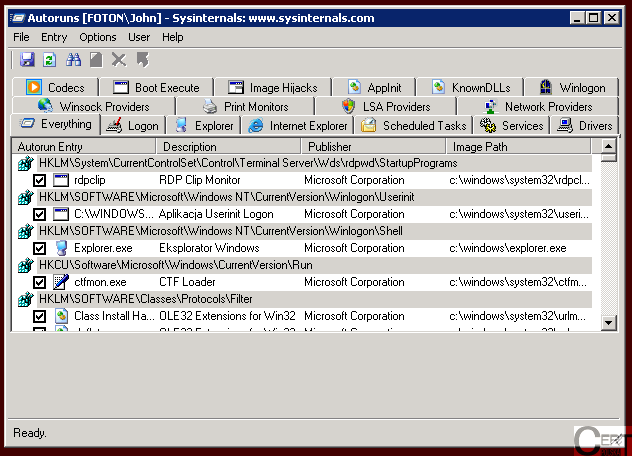
As we can see, this application is quite complex. It lists all the autorun entries it could find on our machine. We will be only interested in two tabs, on which we can find places in which malware usually resides, namely:
and
.
Identification and deactivation of the malicious software
|
 |
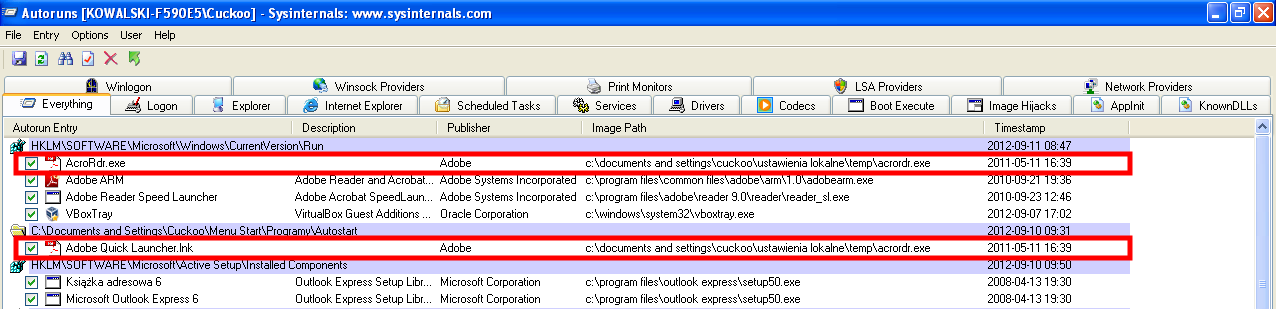
One of the telltale signs of the malware is its location (presented in the column called
). If the entry begins with
then most probably this entry corresponds to the malicious software. In the sample that we obtained, it always pointed to a file called
. It is important to note that this malware can add multiple entries – two of them are presented in the image below. In order to turn them off, we have to click a checkbox next to the entry.
After we turn off all of the suspicious entries and restart the computer we have to check again if the Bank Account Numbers are replaced in the Windows clipboard. If not then we successfully got rid of the infection.