 AutoIt scripts use becomes more and more fashionable for malware obfuscators, cryptors and alike. Especially among the not-so-sophisticated malicious software. Recently we described the phishing attack targeted at Polish users using Booking.com and Allegro.pl. This attacked used AutoIt script (called RazorCrypt) in one of its stages in order to pack the final malware. We observed a somewhat similar campaign (although there are no conclusions about the authors this time) that also used a very interesting AutoIt script and also was targeting Polish users of an auction website Allegro.pl.
AutoIt scripts use becomes more and more fashionable for malware obfuscators, cryptors and alike. Especially among the not-so-sophisticated malicious software. Recently we described the phishing attack targeted at Polish users using Booking.com and Allegro.pl. This attacked used AutoIt script (called RazorCrypt) in one of its stages in order to pack the final malware. We observed a somewhat similar campaign (although there are no conclusions about the authors this time) that also used a very interesting AutoIt script and also was targeting Polish users of an auction website Allegro.pl.
You bought a laptop, here’s your Bitcoin miner invoice
We have received an information from users about the new malware campaign, which again uses Allegro.pl (Polish online auction website) to encourage users to click in a link. This e-mail informed that user won an auction for
and referred to an auction number
. Screenshot of an e-mail message is provided below.
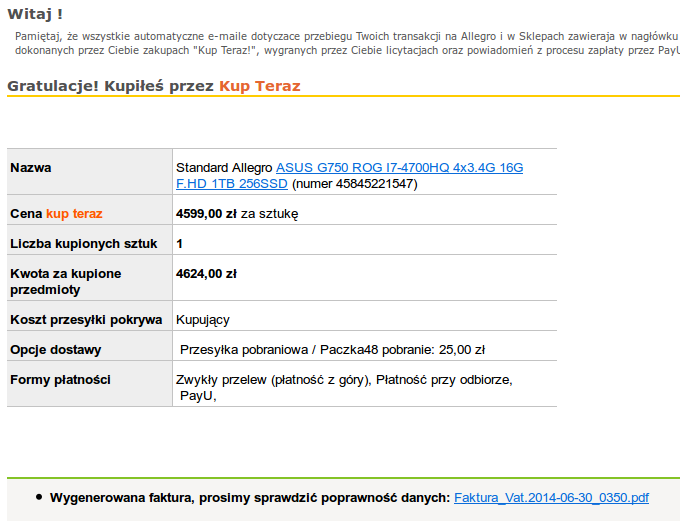
Message contained two links – one to a supposed “invoice” and a second one to the auction. Both were leading to a
file and had an icon representing a PDF file. Additionally, it also opened a real PDF file containing a real-looking invoice (presented below). Unfortunately, a malware, used to mine Bitcoins, was also being run in the background.
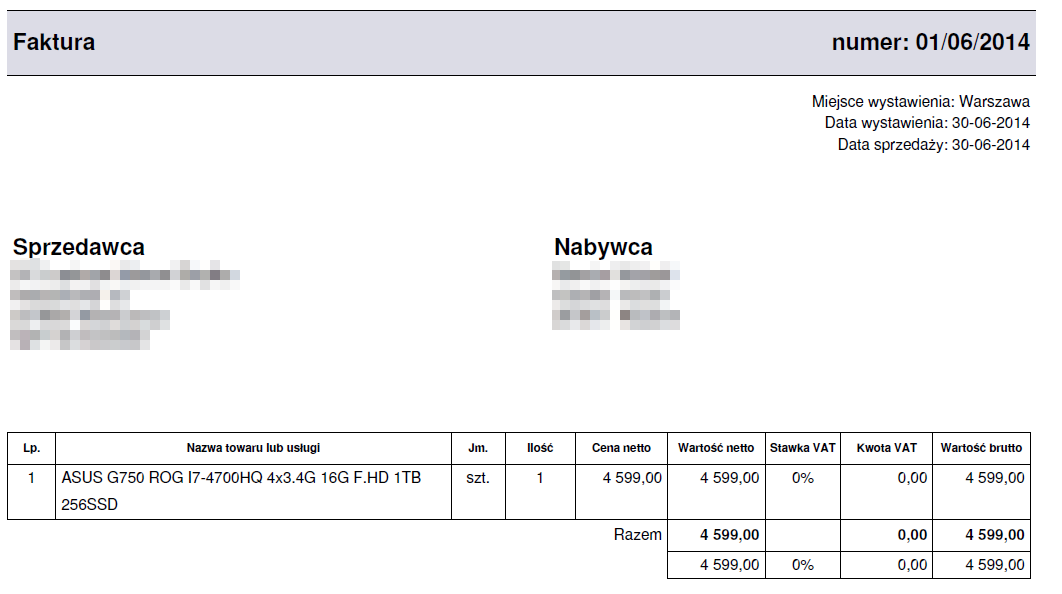
PDF metadata contained an IP address
in the
field and hostname
in the
field. Creation date is set to 30th June and the PDF title is
.
Your invoice is conveniently provided in PDF, AutoIt, PE, VBS, COM and BAT simultaneously
The “invoice” exe file is actually an SFX file, which unpacks several files. The main file is
, which contains a invoice presented above. This PDF file does not contain any exploit. Instead of exploiting software, it unpacked few other files in the
directory.
- VBS (Visual Basic Script) file, which runs a batch file.
- BAT file, which runs AutoIt script from an interpreter.
- AutoIt interpreter with COM file extension.
- AutoIt script.
- INI file used by the AutoIt script.
- Encrypted (using RC2) PE file, which contains cpuminer – CPU-based Bitcoin miner.
- Turning off “System Recovery” service.
- Creating BSOD (Blue Screen of Death) using an undocumented, but known call to the WinAPI
<span class="text">NtSetInformationProcess</span>
function.
- Prevention from malware removal. Some deleted files were recreated (e.g. VBS, BAT) and the registry key
<span class="text">HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce</span>
was also recreated.
- Appending additional text to the messages sent using IM and social networks like: Facebook, Skype, Omegle, Steam, Tinychat or Runescape.
- Downloading and running additional software.
- Detecting virtualization by checking if
<span class="text">VboxService.exe</span>
or
<span class="text">VMwaretray.exe</span>is running.
- Controlling the different malware instances using mutex.
- Turning off User Access Control (UAC) by using a registry modifications.
- Turning off the display of hidden and system files.
- Displaying a message box to the user.
Despite realizing relatively trivial task, it uses a lot of different file formats. This may be in order to make the analysis harder for the researchers. Cpuminer logged to
using a
login.
AutoIt script – so many possibilities, none of them used
AutoIt script was the most interesting from all of the dropped files. It was obfuscated by adding a lines starting with white characters and
character, which is how comments are written in AutoIt scripts. When these lines were stripped, a readable script was obtained, with descriptive variable names and comments.
This campaign used only one of this script possibilities – running a RC2 encrypted PE file as another process, using a technique called “process hollowing”. This means that a benign process is created (in this case 32bit
) in a suspended state. Then, decrypted PE is written to a process memory. Then process is resumed and continues running a malware. In this case identification of the malicious process was straightforward, because it was run with a very unusual parameters, at least for Service Host:
However, script has a vast number of features, including:
All of these options were configurable using a INI configuration file.
Summary
Campaign was made in a really convincing way – the notifications looked like real e-mails from Allegro.pl (sans the invoice). The message also used links instead of attachments – probably to bypass some spam/AV filters.
AutoIt scripts are used to conceal malware for some time. Popularity makes them a good product and they become even more sophisticated. They are used not only to decrypt and run the PE file, but also have additional functionalities, like the ones desribed above
Hashes of samples
Below are included MD5 haseshes of some of the analyzed samples.
1f5a9caa675eb71e3767f765fe0a21a8 run.bat
8e14f298b25e60ebf4d7d9c7787b3aff run.vbs
48b8ade376a44ef498bcd3fec0f96d76 script.autoit
f0b0c815ab1c01c336ccc6147253ed0c settings.ini
