 In the last few days we observed a number of new attacks targeting the Polish Android users. Many Polish and foreign blogs reported the phishing e-mails using Kaspersky brand to convience user to install an apk file. Below some details of this attack, including the malware analysis, are provided. Thanks to the cooperation of different actors, C&C server was taken down very quickly. Malware moved to the new C&C and changed its infection vectors. Below we also describe the new (though some may call it vintage) infection vector utilizing the BitTorrent network. We are sure that all of these attacks are performed by the same person or a group that created the VBKlip in the .NET version.
In the last few days we observed a number of new attacks targeting the Polish Android users. Many Polish and foreign blogs reported the phishing e-mails using Kaspersky brand to convience user to install an apk file. Below some details of this attack, including the malware analysis, are provided. Thanks to the cooperation of different actors, C&C server was taken down very quickly. Malware moved to the new C&C and changed its infection vectors. Below we also describe the new (though some may call it vintage) infection vector utilizing the BitTorrent network. We are sure that all of these attacks are performed by the same person or a group that created the VBKlip in the .NET version.
Mail from “Kaspersky”
On the 31th of July and 1st of August some of the Polish Internet users received an e-mail with content similar to the one presented below.
banku pod kątem wykrycia złośliwego oprogramowania.
W skutek skanowania firma Kaspersky wykryła infekcją na Twoim telefonie
z systemem Android
Wykryty wirus jest przeznaczony do okradania kont firmowych zdolny
min. do wykradania kodów SMS, służących do autoryzacji przelewów.
Oznacza to że cyberprzestepcy mogą zatwierdzić dowolny przelew z Twojego konta
bankowego!
Aby zapobiec kradzieży gotówki z Twojego konta prosimy o bezzwłoczną instalację
programu Antywirusowego Kaspersky Mobile Security w urządzeniu mobilnym.
Darmowa wersja programu dla klientów banku została dodana w załączniku
wiadomości.
Mail is written in a way that convinces users that their bank asked Kaspersky to perform a scan of mobile devices of all of the bank clients. This scan supposedly revealed a malware on the user device and Kaspersky asks to install a version of its security suite made specifically for the bank customers.
In reality, a file with the
extension attached to the mail contained an Android RAT called “SandroRat”. Below is the commercial of this tool on one of the forums.
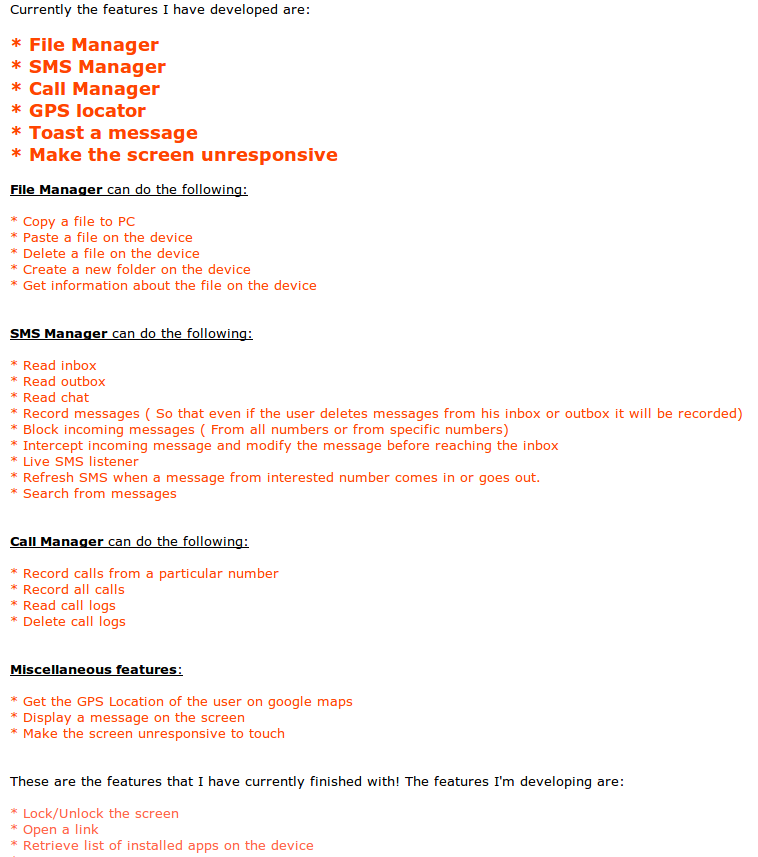
Malware author states that this a FUD (meaning Fully UNdectable). Indeed when the mail was send, very first analysis on the VirusTotal service confirmed that only one of the 53 different antivirus solution detected this sample as a malware. Author states that he also created a similar application with a reversed function – it allows users to control their PC using their Android phone. This application is available in the Google Play store.
Sandrorat – features
Application has a vast features, which can be seen from the permissions it requires in order to run:
android.permission.RECEIVE_SMS
android.permission.INTERNET
android.permission.RECORD_AUDIO
android.permission.READ_EXTERNAL_STORAGE
android.permission.WRITE_EXTERNAL_STORAGE
android.permission.ACCESS_WIFI_STATE
android.permission.READ_PHONE_STATE
android.permission.WRITE_SMS
android.permission.ACCESS_FINE_LOCATION
android.permission.ACCESS_COARSE_LOCATION
android.permission.ACCESS_NETWORK_STATE
android.permission.CAMERA
android.permission.WRITE_CONTACTS
android.permission.READ_CONTACTS
android.permission.SEND_SMS
android.permission.READ_CALL_LOG
android.permission.WRITE_CALL_LOG
android.permission.GET_ACCOUNTS
com.android.browser.permission.READ_HISTORY_BOOKMARKS
android.permission.RECEIVE_BOOT_COMPLETED
android.permission.WAKE_LOCK
android.permission.CALL_PHONE
However, as we mentioned in the E-Security case the fact that application has some permissions does not mean that it will be using them. SandroRat saves all of its configuration in the SQLite database in one two column table. Using the
function it can, based on the supplied commands, redirect short messages to the C&C. It also saves the messages and call metadata in the SQLite database, in order to send them later to the C&C. This, according to the author, is made in order to make sure that even if user deletes message or the call record, the backup version will be sent to the C&C server.
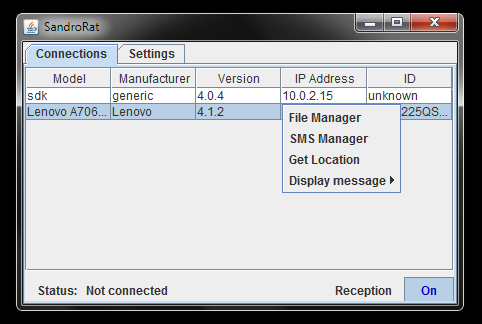
Aplication can also display the “Toast” messages and update itself. There are 39 different commands supported ranging from the “ACK” (to make sure that the bot is online) to calling a number or recording sound using the phone’s microphone. In all of the samples that we have analyzed, classes that make the SandroRat are in the
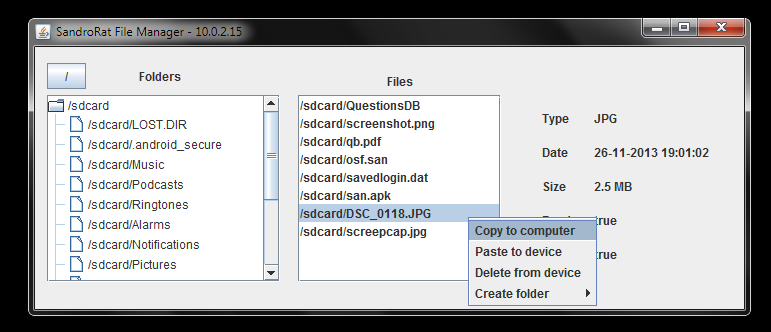
package. Above and below are the screenshots from the control panel, made as a part of the SandroRat commercial.
More detailed analysis can be found on the Kaspersky’s Securelist website.
Unsuccessful spam campaign and new vectors of infection
Spam campaign from the 31th of July and 1st of August was very quickly spotted and thanks to the participation of many actors, Polish users where aware of the threat. This probably was not as successful as the author had imagined and he started to use a new infection vector.
BitTorrent network is, among other things, used to distribute a cracked version of the paid apps, so that users can enjoy all of the features for free. This made the author think that if he were to distribute “full versions” of the popular Android apps he could gain new bots for his network. So he distributed games, including GTA 3 and Assassin’s Creed Pirates, which in reality were just a SandroRat. He also distributed an “unlocker” for the full version of the “BIG! caller ID” app.
In this way gamers who wanted a full version of the game, but did not want to pay for it, were in fact infected with the RAT. This is one of the reasons why applications should only be downloaded from the official and legitimate sources, like the App Stores. That is not to say that BitTorrent is not used to distribute games – just make sure that you are using the right source. Downloading from sources not supported by the application vendor increases the risk of malware infection.
Summary
Vector of infection mentioned above has been seen before – cracked versions of the non-free PC games were circulating in the BitTorrent network. They sometimes also contained an additional piece of code – one that made the gamer a part of the attacker botnet. The same situation was with key generators (or keygens for short) – software that was used to create activation keys for the paid software. Today this method evolves and moves from the PC market to the applications for our smartphones and tablets.
If you have downloaded an application that raises suspicions you can always use the free VirusTotal service to check if this is indeed a malware. However, you must remember that some malware is indeed a FUD – no antivirus detects it. In this case it is better not to install any application not coming from the major App Stores, especially when it requires excessive permissions.
In our opinion this app, apart from the mentioned “bank” in the mail, was not used to steal users OTPs. Instead is was used to steal the private data. Of course, it can also be used to steal OTPs, however the attacker has to also know the login and password to the online banking website and be able to tie it with that client mobile phone. And this task is a harder one.
