 Recently, we obtained a sample of a new Android banking trojan, named GMBot, which tries to be self-contained (i.e. does not need Windows counterpart) and uses application overlay as a poor man’s webinjects substitute. This malware uses known and common techniques, but implements them in a way similar to the webinject-based malware known from Windows OS. This bot’s old source code, written in Java, was also available on a Google-indexed Russian file sharing website. While we want to stress out that GMBot does not do Android webinjects, it is hard not to draw a parallel between webinjects infrastructure and what GMbot does. Is this a glimpse in the future of mobile banking trojans?
Recently, we obtained a sample of a new Android banking trojan, named GMBot, which tries to be self-contained (i.e. does not need Windows counterpart) and uses application overlay as a poor man’s webinjects substitute. This malware uses known and common techniques, but implements them in a way similar to the webinject-based malware known from Windows OS. This bot’s old source code, written in Java, was also available on a Google-indexed Russian file sharing website. While we want to stress out that GMBot does not do Android webinjects, it is hard not to draw a parallel between webinjects infrastructure and what GMbot does. Is this a glimpse in the future of mobile banking trojans?
Dynamic application overlay
Application overlay is a simple technique described in our previous blog entry. It is often used in malicious Android applications in order to impersonate other app. When malicious app checks that user opened online banking app it displays a window on top of that app with a message. User assumes that this message comes from the banking app and is fine with providing login, password or even other data, that she would normally not leave on a phishing website.
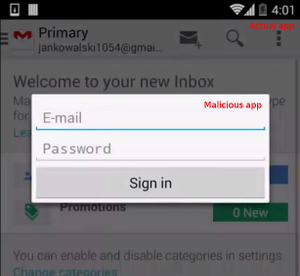
The figure above illustrates this technique. However, up until now, we only saw that this technique was used to present a user with login / password entry form. Instead, GMBot updates a list of app overlay targets and HTML snippets corresponding to them. If user opens the targeted app, GMBot opens the WebView in which it renders the provided HTML. The code below is part of what is used to achieve that.
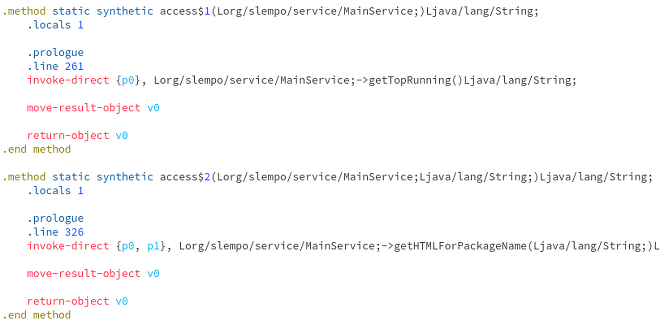
This is almost exactly the same way Zeus and other webinject-based Windows malware uses C&C servers to provide infected users with JavaScript snippets. However, in order to get credit card information, attackers use an old, hardcoded version of app overlay. This is an artifact from a previous version of the app, for which we were able to get the source code. Snippet of this code is presented below.
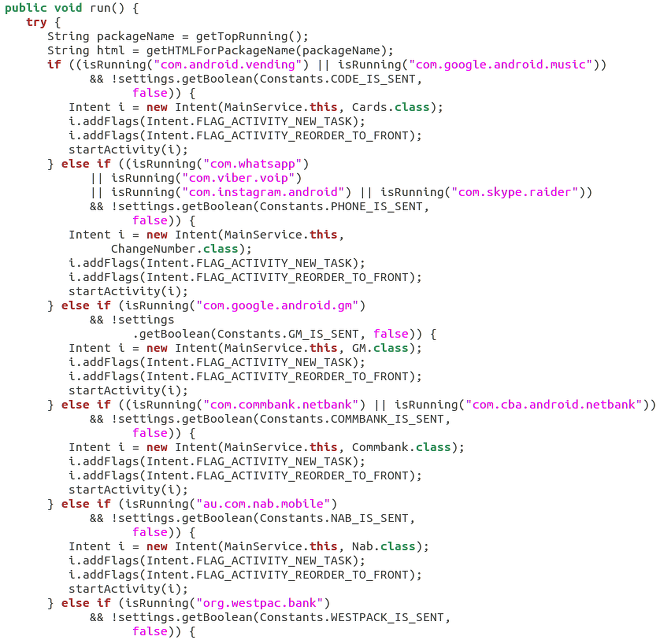
From this old source code we can infer that the author targeted the following applications:
-
<span class="text">com.android.vending</span>
and
<span class="text">com.google.android.music</span>– Google Music and Play for credit card data phishing
-
<span class="text">com.whatsapp</span>
,
<span class="text">com.viber.voip</span>,
<span class="text">com.instagram.android</span>,
<span class="text">com.skype.raider</span>– What’s App, Viber, Instagram and Skype, phishing to change the 2FA number
-
<span class="text">com.google.android.gm</span>
– GMail, login and password phishing
-
<span class="text">com.commbank.netbank</span>
,
<span class="text">com.cba.android.netbank</span>– Commonwealth Bank of Australia
-
<span class="text">au.com.nab.mobile</span>
– NAB Internet Banking
-
<span class="text">org.westpac.bank</span>
– Westpack Bank
-
<span class="text">org.stgeorge.bank</span>
– St.George Mobile Banking
However, this does not hold true for the most recent versions. Apart from that, GMBot is a relatively simple banking trojan that is used to infect users in order to transfer money from their accounts. It requests Device Administrator privileges, mainly in order to be able to perform factory reset. It also can redirect incoming messages in order to send one time passwords to the attackers. One of the interesting features is that it checks if user locale is set to Russian, in which case the trojan does not start. It also sends a basic phone info (manufacturer name, model, OS version, installed app list etc.).
By using the method described above, the attacker needs only to infect the Android phone and there is no need for a Windows counterpart. Attacker can get login and password, using application overlay, and get one time passwords by monitoring incoming text messages. It is worth noting that since Android KitKat, a user would have to set this malicious app as a main messaging application. Otherwise, the text messages will still be visible in the inbox.
Hashes
ac256d630594fd4335a8351b6a476af86abef72c0342df4f47f4ae0f382543ba
62f1a06272b4db982083806c0264f74f4b1339fbd5acfe22ab5d0f0a4ef0a718
