-
Malware stories: Deworming the XWorm

XWorm is a multi-purpose malware family, commonly used as RAT. This post contains a detailed analysis and walk-through the reverse-engineering process.
Read more -
Unpacking what's packed: DotRunPeX analysis

When, what and why As a national CERT we analyse all kinds of incidents. Some of them involve widespread APT campaigns, othertimes we just focus on everyday threats. Recently we got notified about a new malspam campaign targeting Polish users and decided to investigate. It all started with this phishing …
Read more -
Malspam campaign delivering PowerDash – a tiny PowerShell backdoor

In late April we observed a malspam campaign delivering a previously unseen PowerShell malware. We decided to provide an overview of the campaign and some of the malware capabilities. We're also dubbing this malware family as "PowerDash" because of the "/dash" path on C2 server, used as a gateway for bots.
Read more -
A tale of Phobos - how we almost cracked a ransomware using CUDA
For the past two years we've been tinkering with a proof-of-concept decryptor for the Phobos family ransomware. It works, but is impractical to use for reasons we'll explain here. Consequently, we've been unable to use it to help a real-world victim so far. We've decided to publish our findings and tools, in hope that someone will find it useful, interesting or will continue our research. We will describe the vulnerability, and how we improved our decryptor computational complexity and performance to reach an almost practical implementation.
Read more -
Vidar stealer campaign targeting Baltic region and NATO entities

While working on our automatic configuration extractors, we came across a rather strange-looking Vidar sample. The decrypted strings included domain names of such organizations as the NATO Strategic Communications Centre of Excellence, Border Guard of Poland, Estonia and Latvia, and Ministry of the Interior of Lithuania. Automatically extracted strings from …
Read more -
Keeping an eye on CloudEyE (GuLoader) - Reverse engineering the loader

CloudEye (originally GuLoader) is a small malware downloader written in Visual Basic that's used in delivering all sorts of malicious payloads to victim machines. Its primary function is to download, decrypt and run an executable binary off a server (commonly a legitimate one like Google Drive or Microsoft OneDrive). At …
Read more -
What’s up Emotet?
What’s up, Emotet? Emotet is one of the most widespread and havoc-wreaking malware families currently out there. Due to its modular structure, it’s able to easily evolve over time and gain new features without having to modify the core. Its first version dates back to 2014. Back then …
Read more -
Brushaloader gaining new layers like a pro
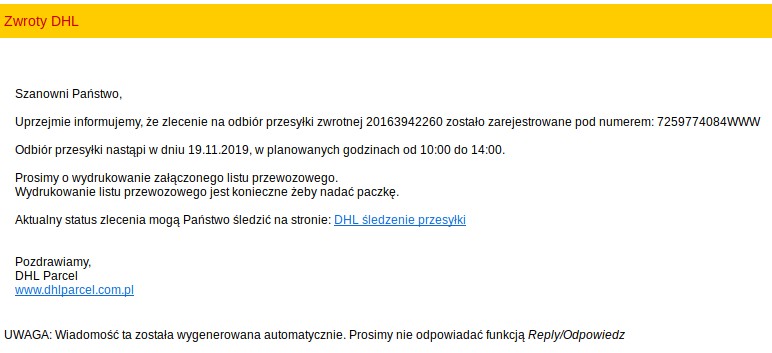
Yo dawg, I heard you like droppers so I put a dropper in your dropper On 2019-11-18 we received a report that some of Polish users have began receiving malspam imitating DHL: In this short article, we’ll take a look at the xls document that has been used as …
Read more -
Dissecting Smoke Loader

Smoke Loader (also known as Dofoil) is a relatively small, modular bot that is mainly used to drop various malware families. Even though it’s designed to drop other malware, it has some pretty hefty malware-like capabilities on its own. Despite being quite old, it’s still going strong, recently …
Read more -
Backswap malware analysis

Backswap is a banker, which we first observed around March 2018. It’s a variant of old, well-known malware TinBa (which stands for “tiny banker”). As the name suggests, it’s main characteristic is small size (very often in the 10-50kB range). In the summary, we present reasoning for assuming …
Read more