-
Brushaloader gaining new layers like a pro
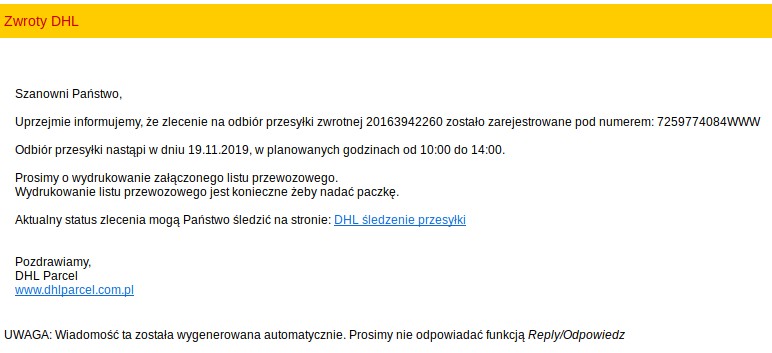
Yo dawg, I heard you like droppers so I put a dropper in your dropper On 2019-11-18 we received a report that some of Polish users have began receiving malspam imitating DHL: In this short article, we’ll take a look at the xls document that has been used as …
Read more -
Dissecting Smoke Loader

Smoke Loader (also known as Dofoil) is a relatively small, modular bot that is mainly used to drop various malware families. Even though it’s designed to drop other malware, it has some pretty hefty malware-like capabilities on its own. Despite being quite old, it’s still going strong, recently …
Read more -
Backswap malware analysis

Backswap is a banker, which we first observed around March 2018. It’s a variant of old, well-known malware TinBa (which stands for “tiny banker”). As the name suggests, it’s main characteristic is small size (very often in the 10-50kB range). In the summary, we present reasoning for assuming …
Read more -
Ostap malware analysis (Backswap dropper)

Malicious scripts, distributed via spam e-mails, have been getting more complex for some time. Usually, if you got an e-mail with .js attachment, you could safely assume it’s just a simple dropper, which is limited to downloading and executing malware. Unfortunately, there is a growing number of campaigns these …
Read more -
Analysis of a Polish BankBot

Analysis of a Polish BankBot Recently we have observed campaigns of a banking malware for Android system, which targets Polish users. The malware is a variant of the popular BankBot family, but differs from the main BankBot samples. Its victims were infected by installing a malicious application from Google Play …
Read more -
A deeper look at Tofsee modules

Tofsee is a multi-purpose malware with wide array of capabilities – it can mine bitcoins, send emails, steal credentials, perform DDoS attacks, and more. All of this is possible because of its modular nature. We have already published about Tofsee/Gheg a few months ago – https://www.cert.pl/en/news …
Read more -
Ramnit – in-depth analysis

If we look on Ramnit’s history, it’s hard to exactly pin down which malware family it actually belongs to. One thing is certain, it’s not a new threat. It emerged in 2010, transferred by removable drives within infected executables and HTML files. A year later, a more …
Read more -
Mole ransomware: analysis and decryptor

Mole ransomware is almost month old ransomware (so it’s quite old from our point of view), that was distributed mainly through fake online Word docs. It’s a member of growing CryptoMix family, but encryption algorithm was completely changed (…again). We became interested in this variant after victims contacted …
Read more -
Analysis of Emotet v4

Introduction Emotet is a modular Trojan horse, which was firstly noticed in June 2014 by Trend Micro. This malware is related to other types like Geodo, Bugat or Dridex, which are attributed by researches to the same family. Emotet was discovered as an advanced banker – it’s first campaign targeted …
Read more -
Evil: A poor man’s ransomware in JavaScript

Introduction Initially Evil was brought to our attention by an incident reported on 2017-01-08. By that time the Internet was completely silent on that threat and we had nothing to analyze. We found first working sample day later, on 2017-01-09. In this article we will shortly summarize our analysis and …
Read more