-
Malspam campaign delivering PowerDash – a tiny PowerShell backdoor

In late April we observed a malspam campaign delivering a previously unseen PowerShell malware. We decided to provide an overview of the campaign and some of the malware capabilities. We're also dubbing this malware family as "PowerDash" because of the "/dash" path on C2 server, used as a gateway for bots.
Read more -
A tale of Phobos - how we almost cracked a ransomware using CUDA
For the past two years we've been tinkering with a proof-of-concept decryptor for the Phobos family ransomware. It works, but is impractical to use for reasons we'll explain here. Consequently, we've been unable to use it to help a real-world victim so far. We've decided to publish our findings and tools, in hope that someone will find it useful, interesting or will continue our research. We will describe the vulnerability, and how we improved our decryptor computational complexity and performance to reach an almost practical implementation.
Read more -
Keeping an eye on CloudEyE (GuLoader) - Reverse engineering the loader

CloudEye (originally GuLoader) is a small malware downloader written in Visual Basic that's used in delivering all sorts of malicious payloads to victim machines. Its primary function is to download, decrypt and run an executable binary off a server (commonly a legitimate one like Google Drive or Microsoft OneDrive). At …
Read more -
What’s up Emotet?
What’s up, Emotet? Emotet is one of the most widespread and havoc-wreaking malware families currently out there. Due to its modular structure, it’s able to easily evolve over time and gain new features without having to modify the core. Its first version dates back to 2014. Back then …
Read more -
Brushaloader gaining new layers like a pro
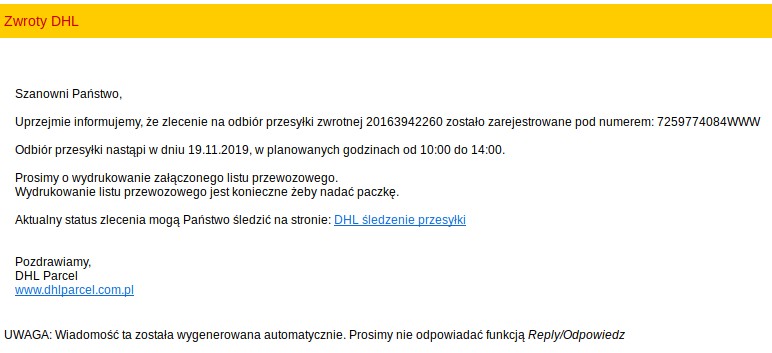
Yo dawg, I heard you like droppers so I put a dropper in your dropper On 2019-11-18 we received a report that some of Polish users have began receiving malspam imitating DHL: In this short article, we’ll take a look at the xls document that has been used as …
Read more -
Detricking TrickBot Loader
TrickBot (TrickLoader) is a modular financial malware that first surfaced in October in 20161. Almost immediately researchers have noticed similarities with a credential-stealer called Dyre. It is still believed that those two families might’ve been developed by the same actor. But in this article we will not focus …
Read more -
Dissecting Smoke Loader

Smoke Loader (also known as Dofoil) is a relatively small, modular bot that is mainly used to drop various malware families. Even though it’s designed to drop other malware, it has some pretty hefty malware-like capabilities on its own. Despite being quite old, it’s still going strong, recently …
Read more -
Ramnit – in-depth analysis

If we look on Ramnit’s history, it’s hard to exactly pin down which malware family it actually belongs to. One thing is certain, it’s not a new threat. It emerged in 2010, transferred by removable drives within infected executables and HTML files. A year later, a more …
Read more