Yo dawg, I heard you like droppers so I put a dropper in your dropper
On 2019-11-18 we received a report that some of Polish users have began receiving malspam imitating DHL:
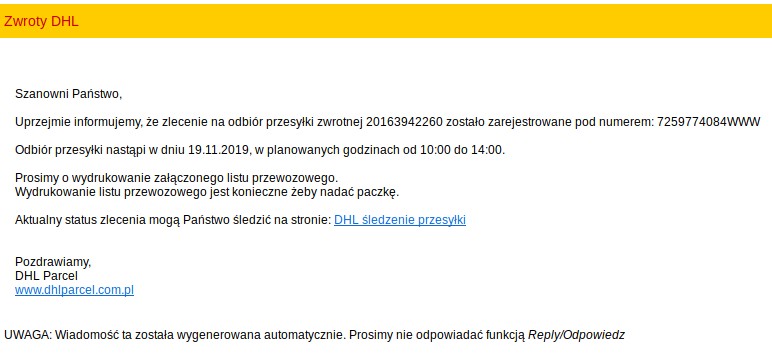
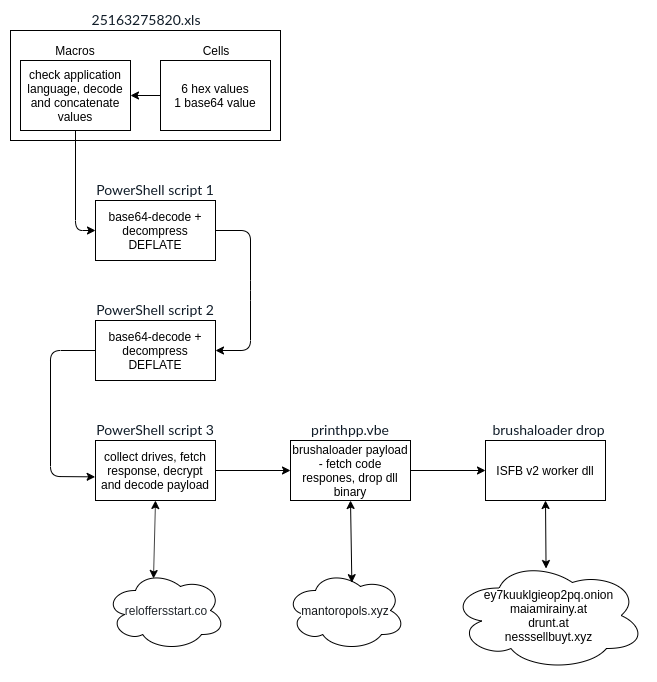
In this short article, we’ll take a look at the xls document that has been used as a (1st stage) dropper distributing another well-known (2nd stage) dropper – brushaloader.
Samples analysed:
- 6a101103486e67f1d8839edd18da773bd9b665ab3df650c9882245d0ee712b8e – 25163275820.xls
- 627294cf0495d2daf8d543aca74bf3cf684673c6a32b8ebf6649f882b362a11a – brushaloader printhpp.vbe
- f25bee3bfe185c6df0ce25cf738f1cc9c72a9ea7f33f6f7545e73d2f3d79b5f8 – brushaloader drop(isfb dll)
While the embedded links did not lead to anything interesting, there was also an .xls file attached, let’s try opening it up:
Interesting…
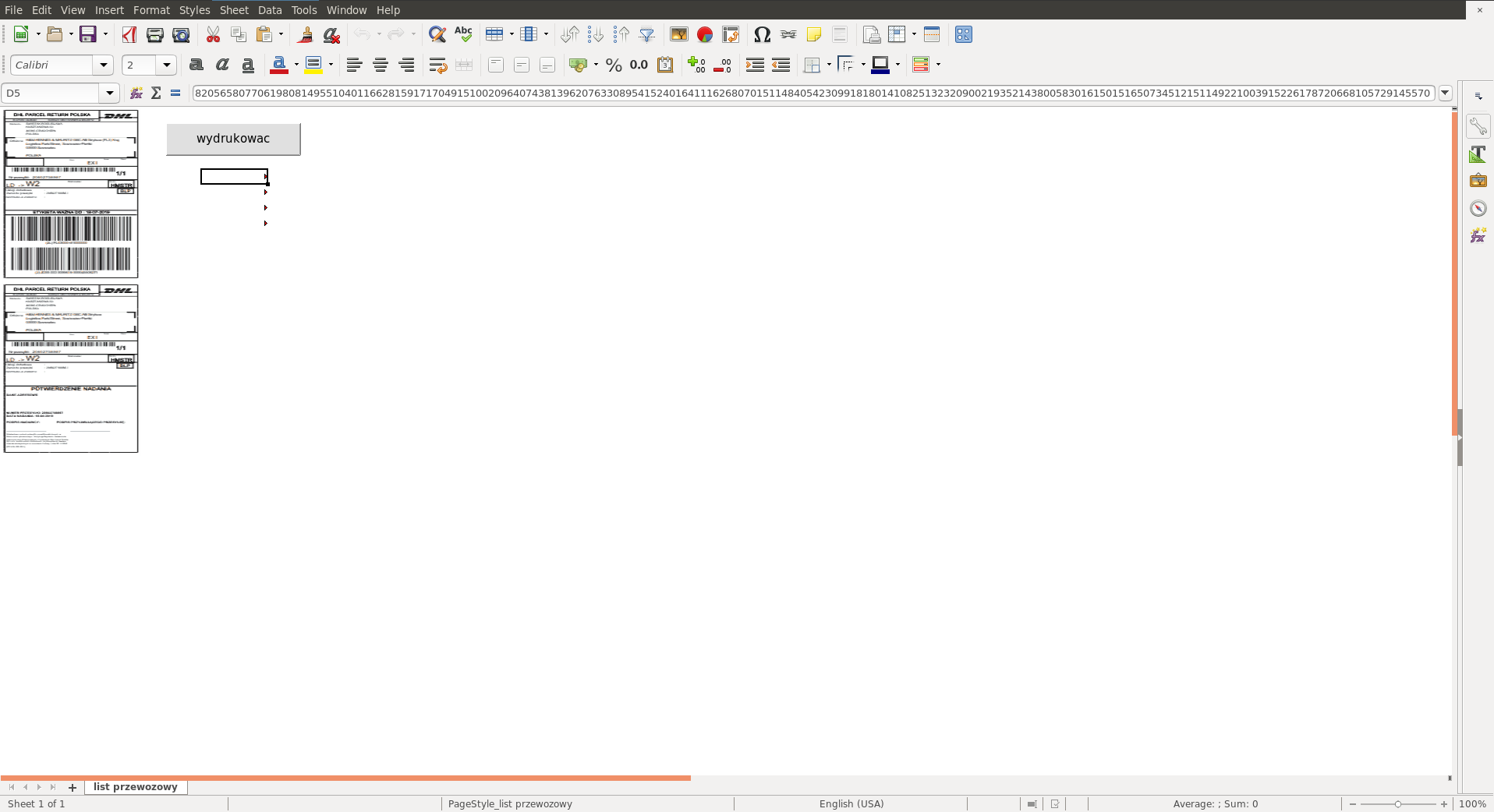
Poking around, we have noticed that some cells have text in them, but their contents were hidden using specific style and formatting; the font size was set to 2 and color was set to white.
Let’s fetch the macro contents to see what’s going on under the hood: ➜ ~olevba 25163275820.xls
The above code is a complete source-code of the macros embedded in the spreadsheet. Taking a closer look we can identify several interesting snippets:
The print button does nothing, probably to encourage users to enable macros in the document.
The payload script will run only on application with language set to Polish (id=1045).
The program will fetch values from cells D5:D8, E5:E8 and J10 which match the fields with embedded data that we have observed earlier.
The cells’ contents are decrypted and concatenated using a custom algorithm. The result is a PowerShell script:
Decompressing the deflate blob can be easily achieved using the following Python script:
Running the script yields the following results:
The resulting script is somewhat obfuscated using strings formatting, we can clean it up with another quick Python script:
Which gives us another PowerShell script with a large base64 blob that contains the next layer:
Decoding the base64 and cleaning up the binary again gives us a yet another PowerShell script:
After some manual formatting we eneded up with the below script:
In short, the script iterates over drive IDs and concatenates them creating a hex-encoded unique id.
That id is then submitted to the c2, which responds with an xor-encrypted payload, that is the first stage vbs of a normal brushaloader campaign.
It can be easilly fetched, decrypted and decoded using this nifty Python script with some help from our malware-analysis library – malduck:
Brushaloader has been described exensively in the past by Proofpoint and Talos, nothing new here.
Let’s focus on the dropped binary instead, Brushaloader used to be used for distribution of Danabot botnet no. 3 in Poland, but some time ago we have observed a shift to ISFB v2.
For this particular sample the config is as follows:
The static config is used to download webinjects and redirects targeting Polish banking sites and email providers.
If you’re interested in receiving information about webinjects targeted at your domain, you might want to check out our injects sharing website: injects.cert.pl
That’s it, if you have any additional questions do not hestitate to reach out to us at @CERT_Polska_en or [email protected]
Thanks to Kafeine from Proofpoint for the ISFB sample.
