Analysis of current threats is one of the most common challenges facing almost any organization dealing with cybersecurity. From year to year, it also becomes a harder nut to crack, being undoubtedly influenced by the growing scale of activities undertaken by criminals and the degree of their advancement. In the face of this situation, efficient exchange of information between researchers is a key issue.
- the user has access to samples that he added to MWDB himself;
- in exchange for adding a sample, the user is provided with information about it obtained in the course of automatic and manual analyses (with the exception that only selected samples are subjected to manual analysis);
- samples located in MWDB can be shared by external entities.
The MWDB system (also known as the “Malware Database”) is a repository for storing malware samples and information acquired during their analysis. The simplest example of this type of data can be the relation of a specific sample with a given malware family, or the addresses of the C&C servers used by it.
Basic description of MWDB
Each user, after logging into the system, can see samples of malicious software in reverse chronological order. Of course it only applies to samples available for particular person (uploaded or derived objects). Each object has the so-called tags that refer to the classification used by CERT Poland during analyzes (e.g. assignment to malware families, specific phishing campaigns, etc).
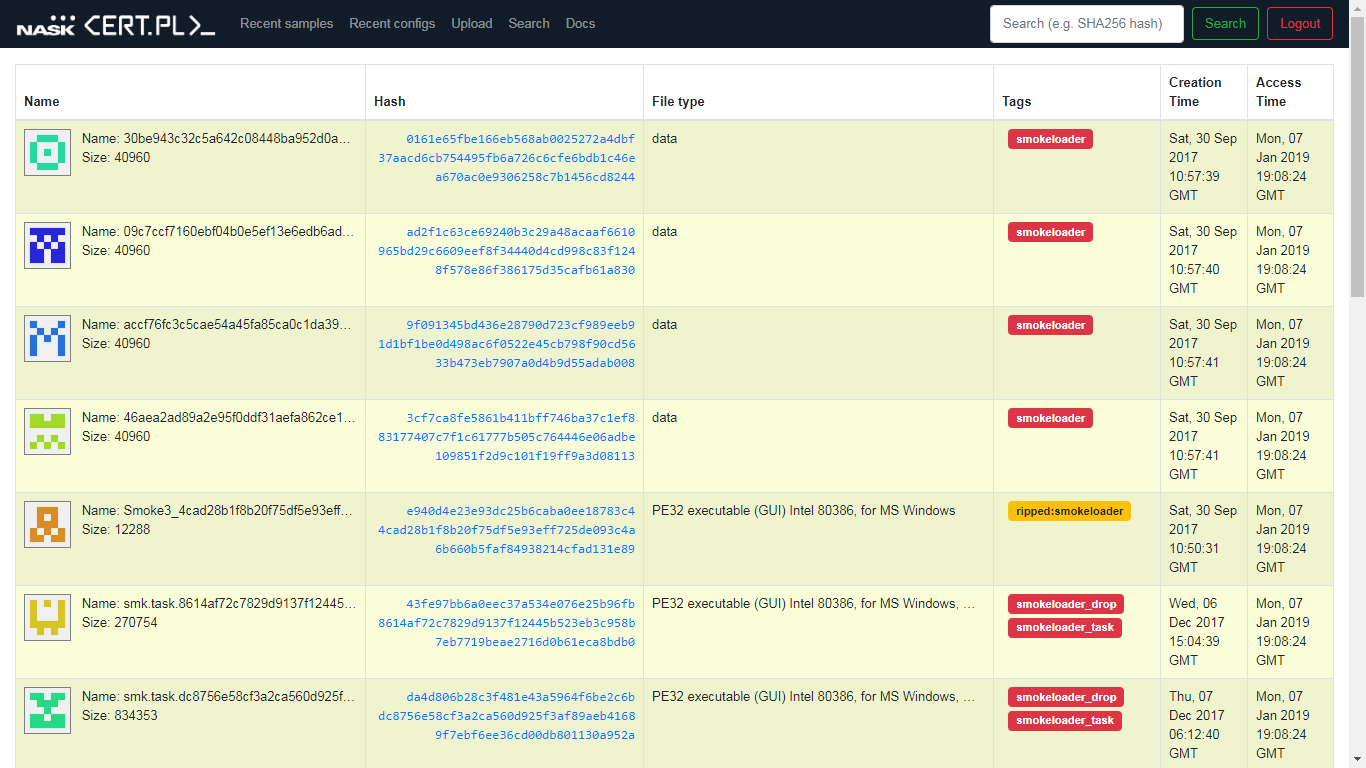 The main page of the MWDB system presenting recently added samples (archive data).
The main page of the MWDB system presenting recently added samples (archive data).
Sample-related information
There is basic data associated with the samples in the MWDB, such as individual cryptographic hashes, file type and file size.
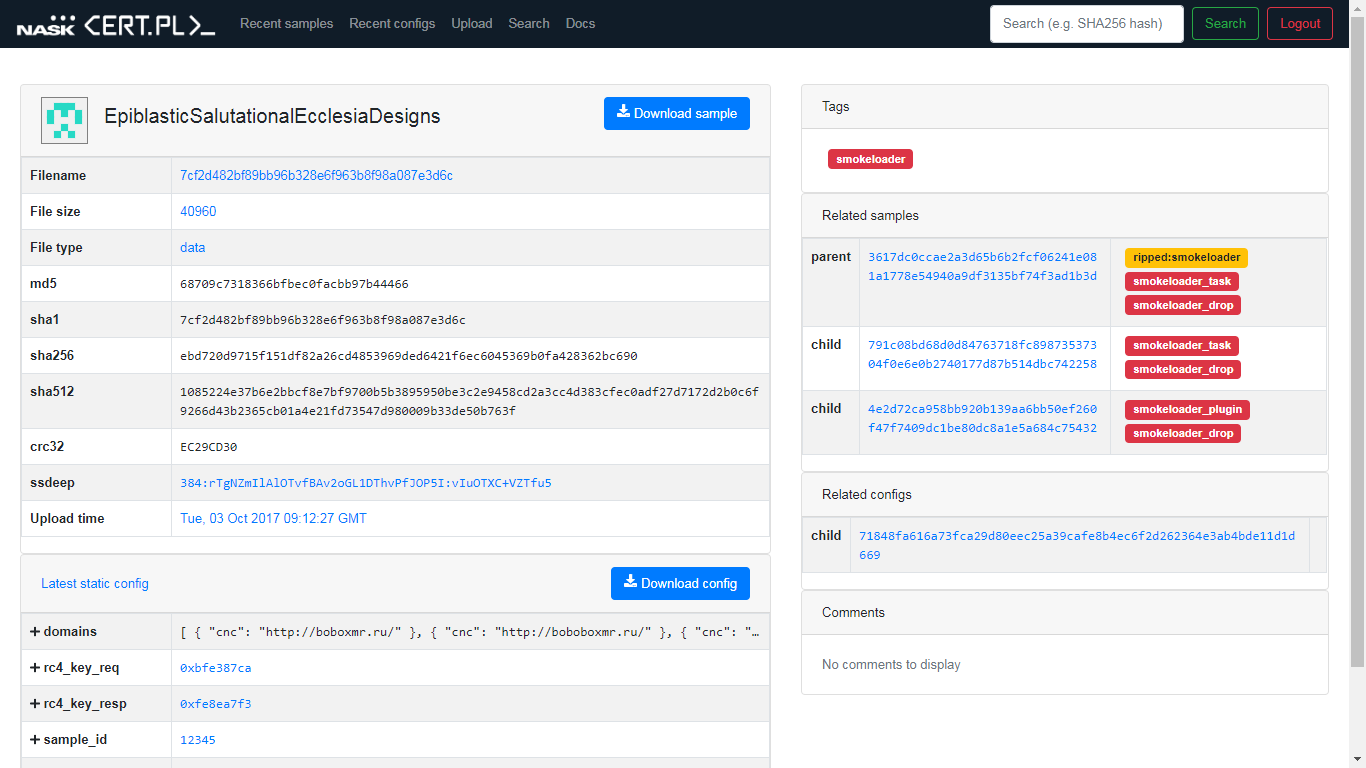
Relationships between related samples are tracked in a form of a tree, which allows for convenient inspection of the path from the dropper to the last stage of the attack.
Detailed view of the sample in MWDB. You are able to see references to the dropper and samples of executable files from the next steps of the infection.
The relations stored in the MWDB system also apply to static and dynamic configurations. The “static” components should be interpreted here as all detailed information that can be extracted directly from a given sample (e.g. the C&C server addresses mentioned above or the encryption keys used). Consequently, the “dynamic” components are all information that is not directly contained in the sample, but is retrieved by it, for example, as a result of connecting to a remote server.
Both the samples and the configuration of the samples are often supported by automated analytical systems, one of which is mtracker described by us last year.
Advanced features
All operations that can be performed via the graphical user interface can also be performed using an API. We also support analysts who use the Python scripting language by providing the mwdblib library, which simplifies the interaction with MWDB.
In case the user has access to a large number of samples, the system offers advanced search functions. You can query similar file names, samples of similar sizes, and specific values in configurations.
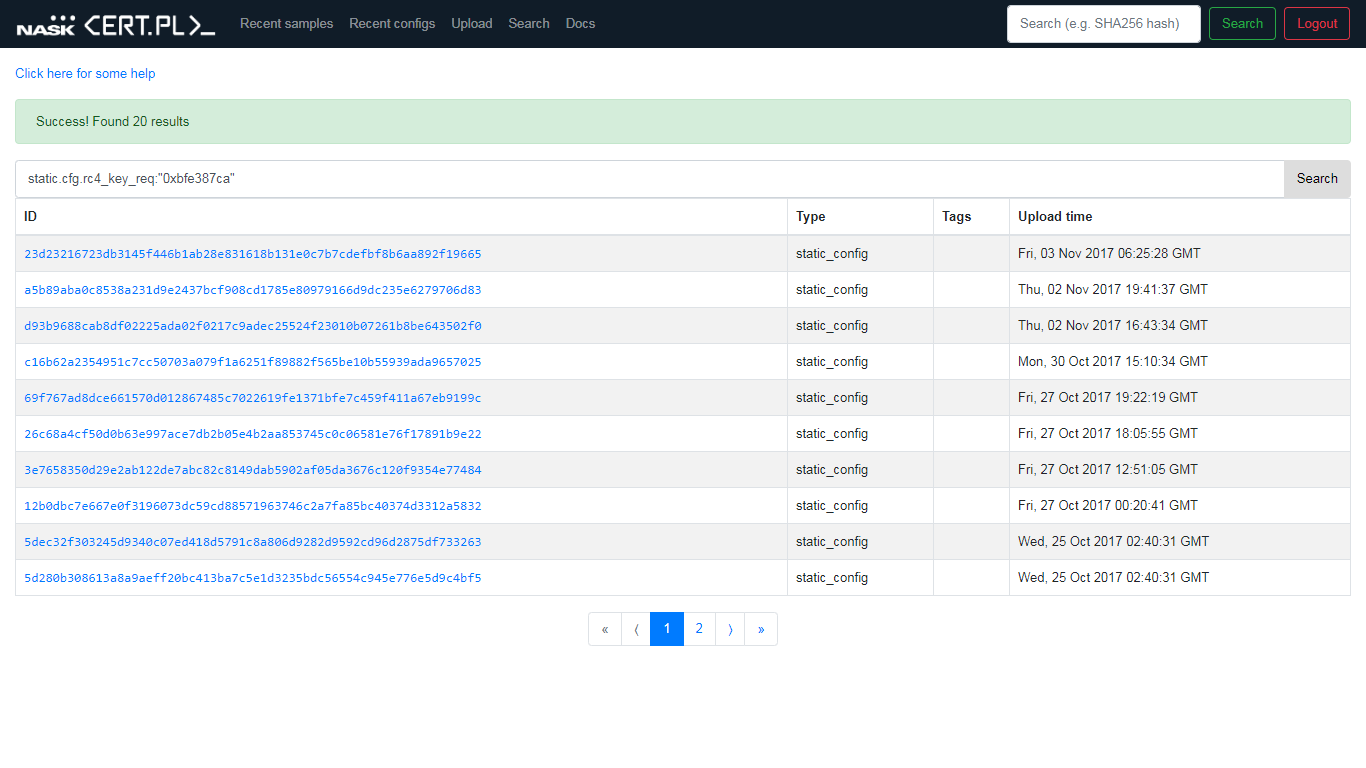 An example of searching for all configurations that contained a specific RC4 key used for request encryption.
An example of searching for all configurations that contained a specific RC4 key used for request encryption.
Access conditions
Third party access to the system is based upon the following rules:
This system is designed for malware researchers. An account can be applied for by people who are able to indicate their affiliation, e.g. as an employee of CERT, a company team responsible for cybersecurity or an academic dealing in malware research.
If you are interested, please use our registration form or contact us at [email protected], while taking into consideration what we reserve the right to respond only to approved applications. Therefore, please pay attention to ensuring the credibility of the application (for example: using a business email, providing your name, surname and position).
Summary
We believe that the exchange of information between CERT Poland and other trusted parties will result in mutual benefit in the form of a better understanding of current threats. We encourage people involved in professional analysis of malicious software to cooperate and to share information within the MWDB.

The contents of this publication are the sole responsibility of NASK PIB and do not necessarily reflect the opinion of the European Union.