-
Nymaim revisited

Introduction Nymaim was discovered in 2013. At that time it was only a dropper used to distribute TorrentLocker. In February 2016 it became popular again after incorporating leaked ISFB code, dubbed Goznym. This incarnation of Nymaim was interesting for us because it gained banking capabilities and became a serious threat …
Read more -
Evil: A poor man’s ransomware in JavaScript

Introduction Initially Evil was brought to our attention by an incident reported on 2017-01-08. By that time the Internet was completely silent on that threat and we had nothing to analyze. We found first working sample day later, on 2017-01-09. In this article we will shortly summarize our analysis and …
Read more -
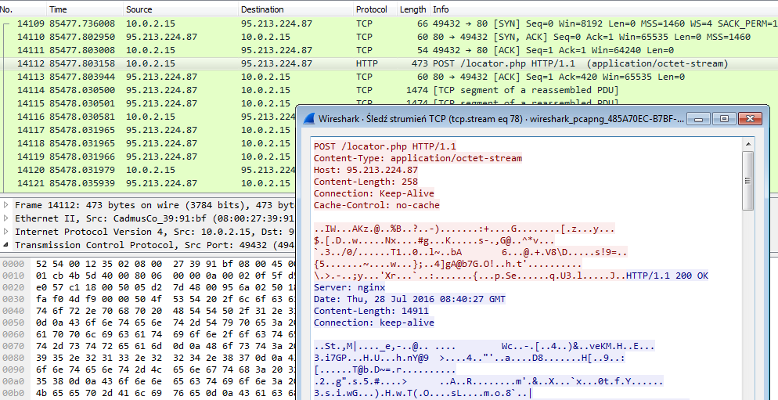
Technical analysis of CryptoMix/CryptFile2 ransomware

Campaign CryptoMix is another ransomware family that is trying to earn money by encrypting victims files and coercing them into paying the ransom. Until recently it was more known as CryptFile2, but for reasons unknown to us it was rebranded and now it’s called CryptoMix. It was observed in …
Read more -
Tofsee – modular spambot

Tofsee, also known as Gheg, is another botnet analyzed by CERT Polska. Its main job is to send spam, but it is able to do other tasks as well. It is possible thanks to the modular design of this malware – it consists of the main binary (the one user downloads …
Read more -
Necurs – hybrid spam botnet
Necurs is one of the biggest botnets in the world – according to MalwareTech there are a couple millions of infected computers, several hundred thousand of which are online at any given time. Compromised computers send spam email to large number of recipients – usually the messages are created to look like …
Read more -
Network traffic periodicity analysis of dark address space
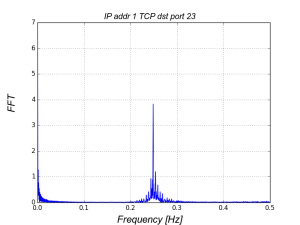
Network traffic directed to dark address space of IPv4 protocol can be a good source of information about current state of the Internet. Despite the fact that no packets should be sent to such addresses, in practice various traffic types can be observed there, for example echoes of Denial of …
Read more -
Agreement on establishment of National CERT

On 4th of July, Minister Anna Streżyńska, Krzysztof Pietraszkiewicz, chairman of Polish Bank Association and Director of NASK Wojciech Kamieniecki signed an agreement on establishing National CERT, intended as communications hub for governement administration and business to coordinate engagement against Internet threats. National CERT is a part of National Cybersecurity …
Read more -
20 June 2016 alex
Polish Internet Security Landscape – CERT Polska Report for 2015

We hereby present you our report on security of Polish internet and of our activities in 2015. We have split the document in following parts: timeline, describing the crucial events, our activities, threat landscape and extensive statistics based on our data. We invite you to read the report and join …
Read more -
Newest addition to a happy family: KBOT

At the beginning of the May here in Poland we have couple of free days. 3rd May is Constitution Day, and May 1st is Labour Day. Most of us use those days to unwind after winter, but some malware authors apparently didn’t: a few weeks ago, our friends started …
Read more -
GMBot: new ways of phishing data from mobile web browsers

GMBot (also known as slempo) was described on our blog on October 2015. This malicious application for phishing login and password associated with a specific user of electronic banking uses known and common techniques of application overlay. It is nothing else but a normal phishing attack, very similar to the …
Read more