
CERT Polska received an Android malware sample. Both the application name (
) and its location (it was downloaded while visiting a popular Polish website, probably as a part of advertisement) may mean that Polish Internet users are targeted. Application sends three Permium-rate SMS, all of which sum to more than 35 PLN (~ 10 USD) and contains rules explaining that we will get an exclusive content in return. This “exclusive content” is in fact another application, which sends even more Premium-rate SMS. Moreover, it is not detected by any antivirus software.
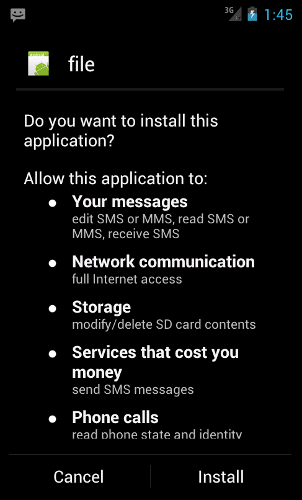
User has to agree to install both applications, and in case of the first one, also click on a button.
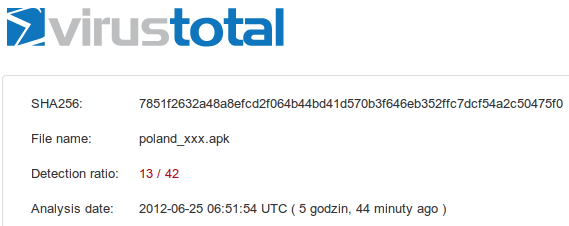
Application 1: poland_xxx.apk
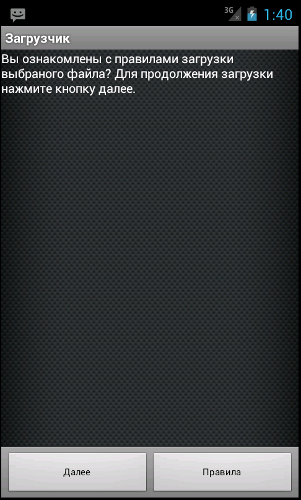
Application is titled “Загрузчик”. It was downloaded during a website visit (so called “drive-by-download” attack). It needs following permissions on an Android platform:
SEND_SMS,
WRITE_EXTERNAL_STORAGE,
READ_EXTERNAL_STORAGE</span>
.
This file is detected by many antiviruses:
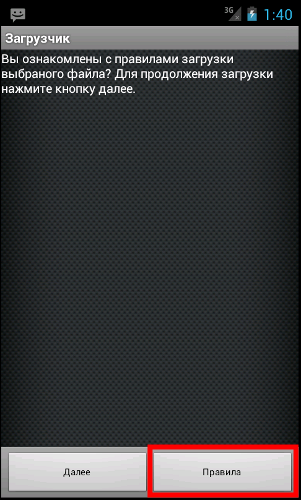
Pfter starting it displays a message presented on the left. As you can see, all messages are in Russian. This may be odd, considering that this malware is spreading on a Polish websites. The message that you see can be translated to: “Do you know rules of downloading files? To continue press Далее”. After clicking on a button entitled “Далее” (Russian: “continue”) two operations are performed. First, C&C server is contacted and a configuration is downloaded. This specifies how many SMS will be send, to which numbers and what will be the content of it. Configuration looks like this:
Country is located based on a geolocation of the phone’s IP address. Thanks to this, phone numbers can be profiled according to the country phone is operating in. Secondly, application downloads file called
and tries to install it.
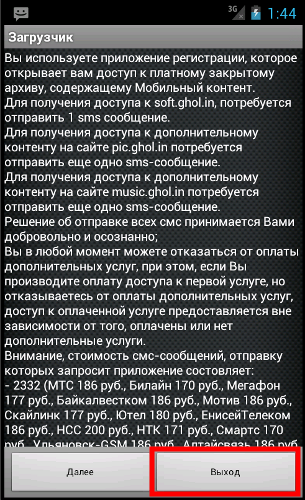
What is interesting, that this application contains a “Rules” section, which can be viewed. It specifies that three Premium-rate SMS will be sent in order to access “exclusive content” on three different websites. At the time of writing, none of this websites exists.
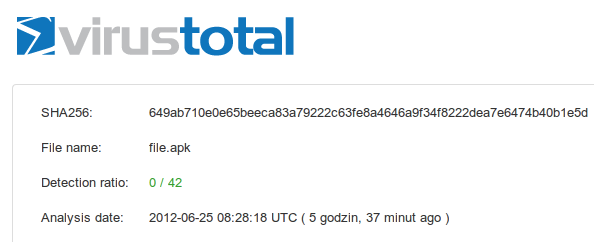
Application 2: file.apk (BotAppActivity)
While the previous application informed user (trough the “Rules” section) that 3 Premium-rate SMS will be send, this one does not. It is a very interesting application, because it is not detected by any antivirus software and makes an Android phone part of a SMS-sending botnet.
Malware communicates with the C&C server and receives configuration from it. Configuration looks as follows:
|
1
|
answer is correct&sendsms74xx@TXT SMSB1 TUR6395 123&sleep 21600000
|
Analysis of this application shows that it supports three types of commands:
,
oraz
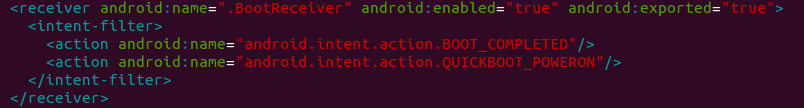
. When communicating with C&C server, application uses an id in order to distinguish infected phones. This can be used to personalize actions on each of the Android devices. Phone sends to C&C server its country code and mobile operator id. C&C server can order phone to send a Premium-rate SMS to any number with any content. Application also makes sure that it can fulfill the C&C task by making the use of Android “Wake Lock”. Additionaly, it also registers a BootReceiver, to make sure that botnet service will start whenever phone starts:
First application is only a “dropper” and can be easily changed, while the second one is considerably more dangerous. Even more so, because it is not detected by any antivirus software.
How not to get infected?
Of course, we should not install any application from an unknown source. Especially the ones that require Internet and SMS access. However, if we run malware analyzed here, we need to click button labeled “Правила” (Russian: “Rules”) and then button called “Выход” (Russian: “exit”), just like showed on the pictures below.
If the application already downloaded
and wants to install it, we can simply deny this request. Our Android device should display a message much like the one presented below.
Application samples
Control sums (both MD5 and SHA1) of the files we have analyzed are below.
17c952f7d65fdf48101011729bd5bad7 file.apk
8c9120f34b38e8449db63f437aa7226f5c106098 file.apk
