-
ClickFix in action: how fake captcha can lead to a company-wide infection

We assisted a large organisation in the investigation and remediation of a live malware infection caused by a successful Fake Captcha attack. In this report, we summarize our observations and publish an in-depth malware analysis.
Read more -
Energy Sector Incident Report - 29 December 2025
CERT Polska presents a report on the analysis of an incident in the energy sector that occurred on 29 December 2025. The attacks were destructive in nature and targeted wind and photovoltaic farms, a large combined heat and power plant, and a company from the manufacturing sector. The publication aims to raise awareness of the risks associated with sabotage in cyberspace.
Read more -
Analysis of NGate malware campaign (NFC relay)

CERT Polska has observed new samples of mobile malware in recent months associated with an NFC Relay (NGate) attack targeting users of Polish banks.
Read more -
UNC1151 exploiting Roundcube to steal user credentials in a spearphishing campaign

CERT Polska is observing a malicious email campaign conducted by the UNC1151 group against Polish entities, exploiting a vulnerability in the Roundcube software.
Read more -
Deobfuscation techniques: Peephole deobfuscation
In this article we describe a basic deobfuscation technique by leveraging a code snippet substitution.
Read more -
Annual report from the actions of CERT Polska 2024

Another year of CERT Polska’s activities is behind us. An absolutely record-breaking year, if we take into account practically all the statistics cited in our previous reports. Behind these numbers is the daily work of experts who care for the safety of Poles online every day. This year’s report is about this work, the key challenges we face and the threats we analyse.
Read more -
Meta is not adequately meeting the demands of CERT Polska

The problem of scammers exploiting social media platforms continues to persist. Meta has yet to fulfill all the recommendations made last year by experts from the CERT Polska team at NASK, which were intended to enhance the safety of Polish social media users.
Read more -
Deprecation of the first version of Dangerous websites Warning List

The Dangerous websites Warning List will soon be five years old. Over this time it stopped millions of attempts to connect to malicious domains and has become our most effective tool in the fight against phishing websites.
Read more -
CERT Polska expectations from Meta regarding the problem of fraud on its social media platforms

The material on social media fraud is visible now in Meta's services, but CERT Polska's position remains unchanged. We need solutions that will increase the security of Polish users.
Read more -
Ad fraud on large online platforms
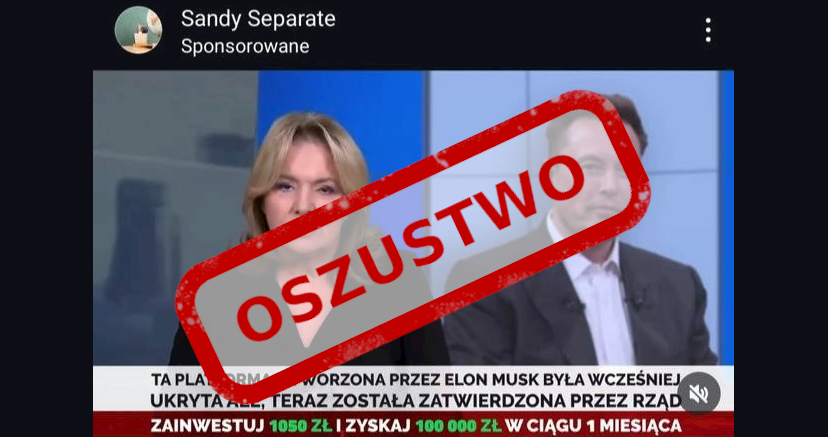
Fraudsters on social media lure users with fake ads promising easy money from celebrities or insider access to government investment programs. These advertisements lead to harmful websites designed to trick or exploit users.
Read more