-
Ad fraud on large online platforms
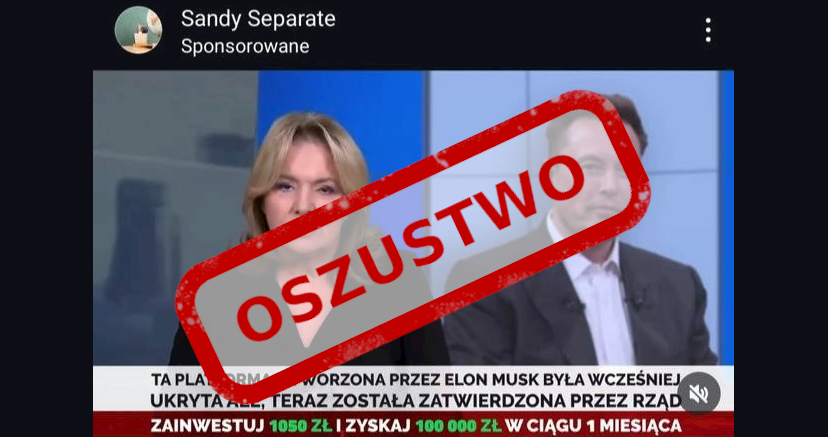
Fraudsters on social media lure users with fake ads promising easy money from celebrities or insider access to government investment programs. These advertisements lead to harmful websites designed to trick or exploit users.
Read more -
Vulnerability in TCL Camera software

Path Traversal vulnerability (CVE-2024-11136) has been found in TCL Camera software.
Read more -
Vulnerability in DInGO dLibra software

Reflected XSS vulnerability (CVE-2024-7124) has been found in Poznan Supercomputing and Networking Center's DInGO dLibra software.
Read more -
Privilege escalation in PAX POS terminals software

Privilege escalation vulnerability (CVE-2023-42133) has been found in PAX Android based POS terminals.
Read more -
Vulnerability in Redlink SDK

Resource Injection vulnerability (CVE-2024-6051) has been found in Vercom S.A. Redlink SDK.
Read more -
Vulnerabilities in MegaBIP software

2 new vulnerabilities (CVE-2024-6662 and CVE-2024-6880) have been found in MegaBIP software.
Read more -
Vulnerabilities in HyperView Geoportal Toolkit software

CERT Polska has received a report about 2 vulnerabilities (CVE-2024-6449 and CVE-2024-6450) found in HyperView Geoportal Toolkit software.
Read more -
Vulnerability in ConnX ESP HR Management software

Stored XSS vulnerability (CVE-2024-7269) has been found in ConnX ESP HR Management software.
Read more -
Vulnerability in KAON AR2140 routers firmware

Command Injection vulnerability (CVE-2024-3659) has been found in KAON AR2140 routers firmware.
Read more -
Vulnerabilities in EZD RP software

CERT Polska has received a report about 3 vulnerabilities (from CVE-2024-7265 to CVE-2024-7267) found in EZD RP software.
Read more