-
In-depth look at Kippo: an integration perspective

Brute-force (dictionary) attacks on Secure Shell (SSH) services remain popular on the Internet. Although hardly a sophisticated type of attack, it is relatively effective, and one of the most common intrusion vectors for UNIX servers. Kippo is a low-interaction honeypot emulating the SSH service. The honeypot can be used to …
Read more -
SECURE 2013 Call for Speakers is Now Open

SECURE is a conference dedicated entirely to IT security and addressed to administrators, security team members and practitioners in this field. SECURE’s unique feature is the organisers’ commitment to providing participants with reliable information about everything that is current and meaningful in IT security. A high professional level of …
Read more -
Virut botnet report

At the end of January and the beginning of February 2013 NASK (Research and Academic Computer Network) — the .pl ccTLD Registry — and its security team CERT Polska took over 43 .pl domains used to control the Virut botnet and to spread malicious applications. As a result of this action, all …
Read more -
23 January 2013 CERT Polska
Honeyspider Network 2.0

The project is a joint venture between NASK/CERT Polska (Poland) and National Cyber Security Centre (Netherlands). Goal of this system is to determine whether a site is malicious to the end-user. Scalability and ability to combine output from multiple client honeypots makes it an effective way of detecting malicious …
Read more -
NASK shuts down dangerous Virut botnet domains

NASK has taken over multiple domains used for cybercrime activities, making their further usage for illegal purposes impossible. The domain names were used to spread and control dangerous malware known as “Virut” . NASK’s actions are aimed at protecting Internet users from threats that involved the botnet built with Virut-infected …
Read more -
15 October 2012 CERT Polska
New paper on data sharing published

In September this year CERT Polska participated in the “Information Assurance and Cyber Defense” symposium organized by NATO’s Science and Technology Organization. Our paper, titled “Proactive Detection and Automated Exchange of Network Security Incidents”, investigates issues related to sharing security-related data among CERTs and other organizations. We attempted to …
Read more -
Dorkbot likes to socialize and steals more than you can imagine
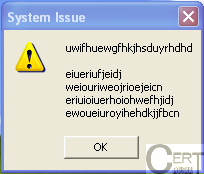
Recently there have been numerous reports about a new malware spreading through Skype. Since a couple of days, CERT Polska has also been taking an active role in disabling the Dorknet worm. A Polish security portal Niebezpiecznik.pl (article in Polish) mentioned that it also targets Polish users. We acquired …
Read more -
14 September 2012 CERT Polska
Do you really need Java?
In late August, Oracle has decided to release Java updates before the planned publication date on October 16 CPU (Critical Patch Update). According to reports update contains four security fixes. This year Oracle has already introduced 32 security fixes across all Java SE products. The immediate cause for the release …
Read more -
More human than human – Flame’s code injection techniques

Flame aka Flamer aka Skywiper is a sophisticated trojan application discovered in 2012. Since then it has been the subject of extensive analysis by malware research community. The trojan has been recognized as extraordinarily complicatied, with a modular design and advanced algorithms. The degree of Flame’s complexity raised many …
Read more -
Ransomware: how to remove it, even when the computer does not boot?

We have recently published an article (in Polish) about ransomware malware (mainly WeelsOf) spreading in Poland. This kind of ransomware was initally mentioned on the abuse.ch blog: https://www.abuse.ch/?p=3718. It demands 100 Euro or 500 PLN in order to unlock our computer. We also published …
Read more