-
Detricking TrickBot Loader
TrickBot (TrickLoader) is a modular financial malware that first surfaced in October in 20161. Almost immediately researchers have noticed similarities with a credential-stealer called Dyre. It is still believed that those two families might’ve been developed by the same actor. But in this article we will not focus …
Read more -
Recommendations on mitigation of man-in-the-middle phishing attacks (evilginx2/Modlishka)

CERT Polska has observed an interesting phishing technique used in attack against users of a popular Polish content aggregator. We have also noticed the emergence of a new tool called “Modlishka” whose purpose is to simplify and automate phishing attacks. In this article, we describe the way these highly-automated attacks …
Read more -
MWDB – our way to share information about malicious software
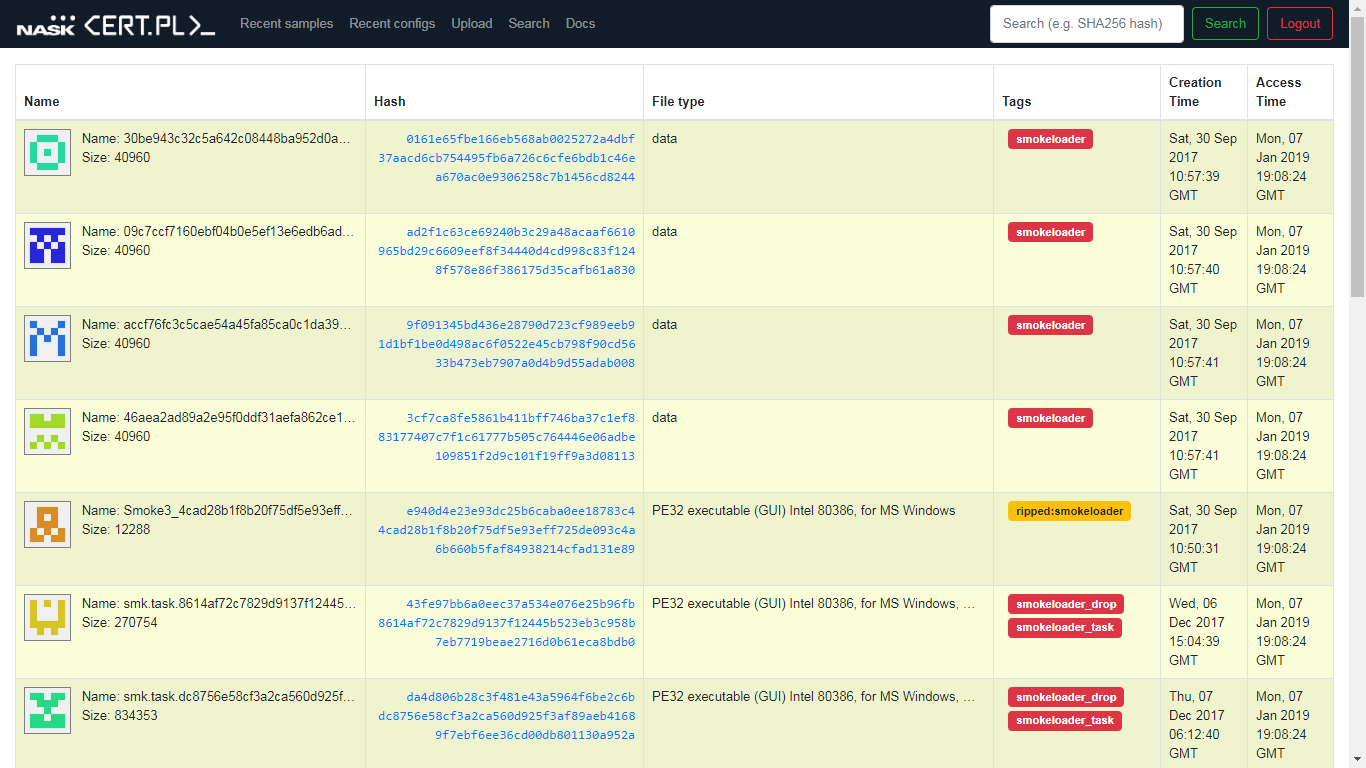
Analysis of current threats is one of the most common challenges facing almost any organization dealing with cybersecurity. From year to year, it also becomes a harder nut to crack, being undoubtedly influenced by the growing scale of activities undertaken by criminals and the degree of their advancement. In the …
Read more -
Dissecting Smoke Loader

Smoke Loader (also known as Dofoil) is a relatively small, modular bot that is mainly used to drop various malware families. Even though it’s designed to drop other malware, it has some pretty hefty malware-like capabilities on its own. Despite being quite old, it’s still going strong, recently …
Read more -
Technical aspects of CTF contest organization

CTF competitions often turn out to be a great amusement, but they also play a very important role in training of IT security specialists. Such kinds of challenges are challenging both to contestants and organizers. This article will describe organizational aspects related to such competitions, taking European Cyber Security Challenge …
Read more -
n6 released as open source

We are happy to announce that another system developed by our team, n6 (Network Security Incident eXchange), has been released to the community on an open source licence. n6 is our in-house developed platform for automated gathering, processing and distribution of information on security threats. It acts as a data …
Read more -
Backswap malware analysis

Backswap is a banker, which we first observed around March 2018. It’s a variant of old, well-known malware TinBa (which stands for “tiny banker”). As the name suggests, it’s main characteristic is small size (very often in the 10-50kB range). In the summary, we present reasoning for assuming …
Read more -
Ostap malware analysis (Backswap dropper)

Malicious scripts, distributed via spam e-mails, have been getting more complex for some time. Usually, if you got an e-mail with .js attachment, you could safely assume it’s just a simple dropper, which is limited to downloading and executing malware. Unfortunately, there is a growing number of campaigns these …
Read more -
SECURE 2018 – Call for Speakers

Call for Speakers for SECURE 2018 is now open. If you have an interesting topic and would like to share your ideas with a crowd of Polish and international IT security specialists, please consider submitting your proposal. You will find all applicable information below. SECURE 2018 will be held on …
Read more -
Mtracker – our take on malware tracking

High-level overview CERT Polska collaborates in SISSDEN (Secure Information Sharing Sensor Delivery event Network) project. One of its goals is to create feeds of actionable security information, that will be further processed by relevant entities (like security and academic researchers, CERTs, LEAs etc.). Mtracker is going to be one of …
Read more