-
Dorkbot botnets disruption

CERT Polska has partnered together with Microsoft, ESET and law enforcement agencies including US-CERT/DHS, FBI, Interpol and Europol in activities aimed at disrupting of the Dorkbot malware family. This disruption – which includes sinkholing of the botnet’s infrastructure – took place yesterday. Dorkbot is a well-known family of malware, operating …
Read more -
Talking to Dridex (part 0) – inside the dropper
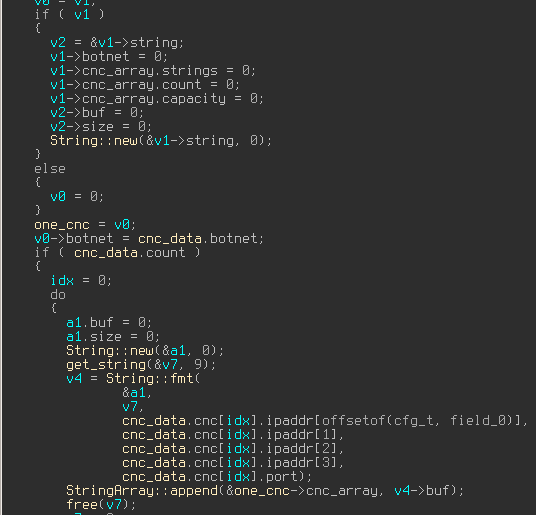
Intro Dridex mostly comes to us as spam which contains a .doc with some macros, responsible for downloading a dropper. One can quickly analyze it using oledump.py and looking through vbscript, or naturally, just try to run it in a sandbox and obtain the dropped files. CFG extraction After …
Read more -
14 October 2015 Łukasz Siewierski #actors #android #e-banking #malware #postal group #ransomware #trojan
The Postal Group

During SECURE conference we have presented our findings about criminal group, which we called “Postal Group” (“Grupa pocztowa”) based on theris modus operandi. Detailed research regarding the group have been gathered in the form of report available under the link below. PDF During the SECURE conference, we presented a talk …
Read more -
A funny little obfuscation technique
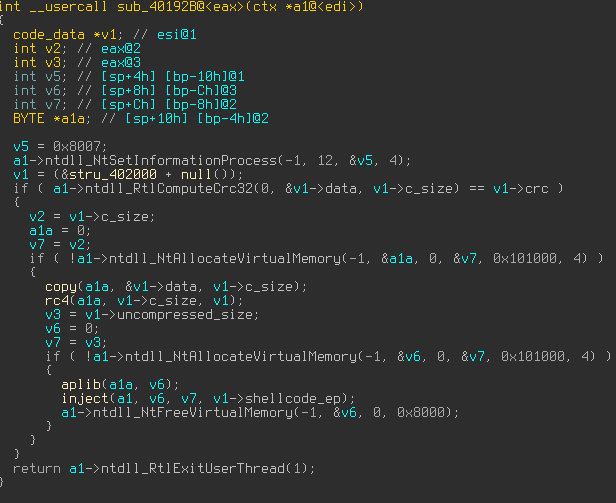
Recently we ran across a quite an interesting sample, which used an interesting obfuscation technique that was beautiful in its simplicity. But before we dive in, let us provide some background for it. One of the easier and most common techniques for automatic unpacking is to hook kernel32!WriteProcessMemory and …
Read more -
Smoke Loader poses as an Office plugin

Zaufana Trzecia Strona – a Polish security news portal – informed about a new attack on Polish user’s (link is in Polish) that used a Microsoft Office plugin install wizard as a decoy. In reality, the user not only installed the plugin, but also a malware called Smoke Loader. It allows …
Read more -
Slave, Banatrix and ransomware

In March 2015, S21sec published their analysis of the new e-banking trojan horse targetting Polish users. They named it “Slave”, because such a string was part of a path to one of the shared libraries. We think (in part thanks to the kernelmode.info thread) that Slave was made by …
Read more -
Threats in Polish networks – CERT Polska 2014 report (English version)

Today, we published the annual CERT Polska report in its English version. This report presents the most important trends and observations that we think shaped Polish cybersecurity in 2014. This includes new, upcoming threats, their evolution and our responses to them. In 2014 CERT Polska continued its effort to better …
Read more -
Malware attack on both Windows and Android

On the 7th of May, 2015 we observed a new malicious e-mail campaign, which used the logo and the name of Polish Post Office (”Poczta Polska”). The e-mail supposedly informed about an undelivered package – however, they also included a link which, after several redirects, lead to the download of a …
Read more -
iBanking is back in Poland

iBanking malware was already described on our blog in connection with the attacks targeting Polish e-banking users at the end of 2013. This malware posed as a mobile antivirus application, while in reality it was use to steal one time passwords that were sent via text message. The attack scenario …
Read more -
Banatrix – an indepth look

Of all of the Polish malware families that we have seen last year, Banatrix seems to be the most technologically advanced one. This malware was used to replace the bank account number in the browser memory, however its implementation allowed an attacker to execute any arbitrary code on the victim …
Read more