-
Malware campaign on Polish governmental site

CERT Polska and CERT.GOV.PL recently discovered a website in the gov.pl domain that has been a part of malware campaign at least since the beginning of May 2013. The page contained a JavaScript code that added a hidden iframe which redirected to the exploit kit. Next, with …
Read more -
The “E-Security” app: a new friend of ZitMo

Recently, we obtained a new Android malware sample, which is targeting Polish e-banking users. The application is called “E-Security” and its filename is e-security.apk . It also has a security-related icon shown on the left. The malware is relatively simple, but effective at achieving its goals …
Read more -
Citadel plitfi botnet report

At the end of February 2013 Polish Research and Academic Computer Network and CERT Polska took over 3 domains used by one of the Citadel botnets, known as “plitfi”. All the network traffic from these domains was directed to a sinkhole server controlled by CERT Polska. Today we publish a …
Read more -
Virut botnet report

At the end of January and the beginning of February 2013 NASK (Research and Academic Computer Network) — the .pl ccTLD Registry — and its security team CERT Polska took over 43 .pl domains used to control the Virut botnet and to spread malicious applications. As a result of this action, all …
Read more -
Dorkbot likes to socialize and steals more than you can imagine
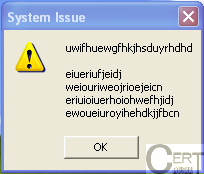
Recently there have been numerous reports about a new malware spreading through Skype. Since a couple of days, CERT Polska has also been taking an active role in disabling the Dorknet worm. A Polish security portal Niebezpiecznik.pl (article in Polish) mentioned that it also targets Polish users. We acquired …
Read more -
More human than human – Flame’s code injection techniques

Flame aka Flamer aka Skywiper is a sophisticated trojan application discovered in 2012. Since then it has been the subject of extensive analysis by malware research community. The trojan has been recognized as extraordinarily complicatied, with a modular design and advanced algorithms. The degree of Flame’s complexity raised many …
Read more -
Ransomware: how to remove it, even when the computer does not boot?

We have recently published an article (in Polish) about ransomware malware (mainly WeelsOf) spreading in Poland. This kind of ransomware was initally mentioned on the abuse.ch blog: https://www.abuse.ch/?p=3718. It demands 100 Euro or 500 PLN in order to unlock our computer. We also published …
Read more -
Android malware sending Premium SMS targeting Polish users

CERT Polska received an Android malware sample. Both the application name ( poland_xxx.apk ) and its location (it was downloaded while visiting a popular Polish website, probably as a part of advertisement) may mean that Polish Internet users are targeted. Application sends three Permium-rate SMS, all of …
Read more -
Analysis of a very social malware

Yesterday Polish security portal, Niebezpiecznik.pl, has informed about a new kind of malware spreading through Facebook (article in Polish). CERT Polska got a sample of this malicious software to analyse. Despite Facebook being not a new attack vector, this malware sample is very interesting. Currently it is detected by …
Read more -
ZeuS – P2P+DGA variant – mapping out and understanding the threat

n the autumn of 2011 we observed new malware infections, which looked similar to Zeus. Subsequent analysis of the malicious software mechanism start up, the process of hiding and storing of configuration indeed verified that it was ZeuS. However, monitoring of infected machines failed to uncover the characteristic communicatation with …
Read more