-
SECURE 2016 – Call for Speakers

SECURE, held on 25th and 26th of October in Warsaw, Poland, is a conference dedicated entirely to IT security and addressed to administrators, security team members and practitioners in this field. SECURE’s unique feature is the organisers’ commitment to providing participants with reliable information about everything that is current …
Read more -
Malicious iBanking application with new uninstall countermeasures

Our CERT laboratory recently received a sample of iBanking malware (along with a malicious JavaScript code snippet associated with it), posing as the mobile Trusteer Rapport antimalware solution. The attack scenario isn’t new, it has been used many times in the past, but recently we see an increase in …
Read more -
09 March 2016 mak
MadProtect, not that mad
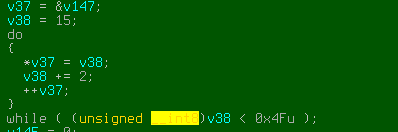
Some weeks ago we stumbled on a packer that our tools could not break. Surprisingly, this is actually not that common since most of the malware in the wild uses some sort of RunPE technique which is relatively trivial to break using simple memory tracing. MadProtect is not any different …
Read more -
Banatrix successor – swapping acct numbers with a Firefox add-on

Our laboratory recently received a sample of malware used for attacks on Polish users of electronic banking. Analysis of this malware gave us reasons to believe, that this is the software written by the authors of Banatrix (which we discussed in greater detail in our earlier posts), Slave and e-mail …
Read more -
Dorkbot botnets disruption

CERT Polska has partnered together with Microsoft, ESET and law enforcement agencies including US-CERT/DHS, FBI, Interpol and Europol in activities aimed at disrupting of the Dorkbot malware family. This disruption – which includes sinkholing of the botnet’s infrastructure – took place yesterday. Dorkbot is a well-known family of malware, operating …
Read more -
Talking to Dridex (part 0) – inside the dropper
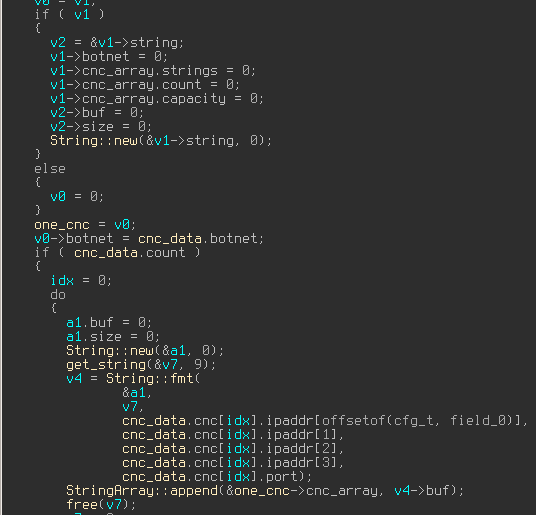
Intro Dridex mostly comes to us as spam which contains a .doc with some macros, responsible for downloading a dropper. One can quickly analyze it using oledump.py and looking through vbscript, or naturally, just try to run it in a sandbox and obtain the dropped files. CFG extraction After …
Read more -
14 October 2015 Łukasz Siewierski #actors #android #e-banking #malware #postal group #ransomware #trojan
The Postal Group

During SECURE conference we have presented our findings about criminal group, which we called “Postal Group” (“Grupa pocztowa”) based on theris modus operandi. Detailed research regarding the group have been gathered in the form of report available under the link below. PDF During the SECURE conference, we presented a talk …
Read more -
GMBot: Android poor man’s “webinjects”

Recently, we obtained a sample of a new Android banking trojan, named GMBot, which tries to be self-contained (i.e. does not need Windows counterpart) and uses application overlay as a poor man’s webinjects substitute. This malware uses known and common techniques, but implements them in a way similar …
Read more -
01 October 2015 piotrb #botnet #detection #detection system #detekcja #dga #DNS #NXDomain #system detekcji
How non-existent domain names can unveil DGA botnets

Domain Generation Algorithms are used in botnets to make it harder to block connections to Command & Control servers and to make it difficult to takeover botnet infrastructure. The main objective of these algorithms is to generate a big number of different domain names which usually look random, like Read more
-
A funny little obfuscation technique
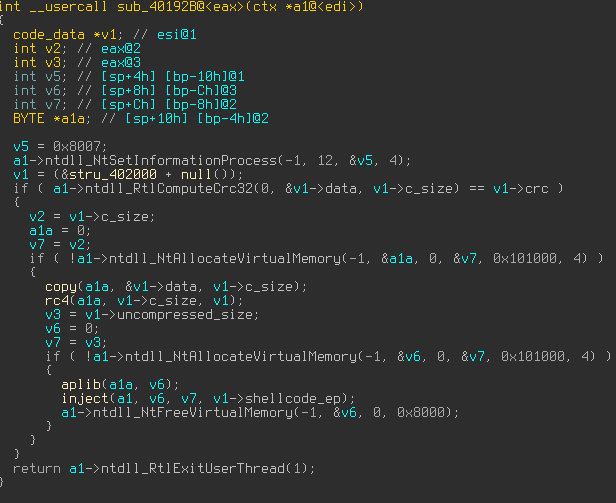
Recently we ran across a quite an interesting sample, which used an interesting obfuscation technique that was beautiful in its simplicity. But before we dive in, let us provide some background for it. One of the easier and most common techniques for automatic unpacking is to hook kernel32!WriteProcessMemory and …
Read more