-
Keeping an eye on CloudEyE (GuLoader) - Reverse engineering the loader

CloudEye (originally GuLoader) is a small malware downloader written in Visual Basic that's used in delivering all sorts of malicious payloads to victim machines. Its primary function is to download, decrypt and run an executable binary off a server (commonly a legitimate one like Google Drive or Microsoft OneDrive). At …
Read more -
Set up your own malware analysis pipeline with Karton

We proudly announce that today we open-source a large part of our analysis framework and pipeline! If you want to try it – check out Karton project on GitHub. What is karton? Karton is a robust framework for lightweight and flexible analysis backends. It can be used to connect malware analysis …
Read more -
Set up your own malware repository with MWDB Core

We proudly announce that the open-source version of MWDB Core has been released! If you want to try it – check out mwdb-core project on GitHub. What is MWDB Core? MWDB Core is a malware repository for automated malware collection and analysis systems, developed by CERT Polska. You can set it …
Read more -
What’s up Emotet?
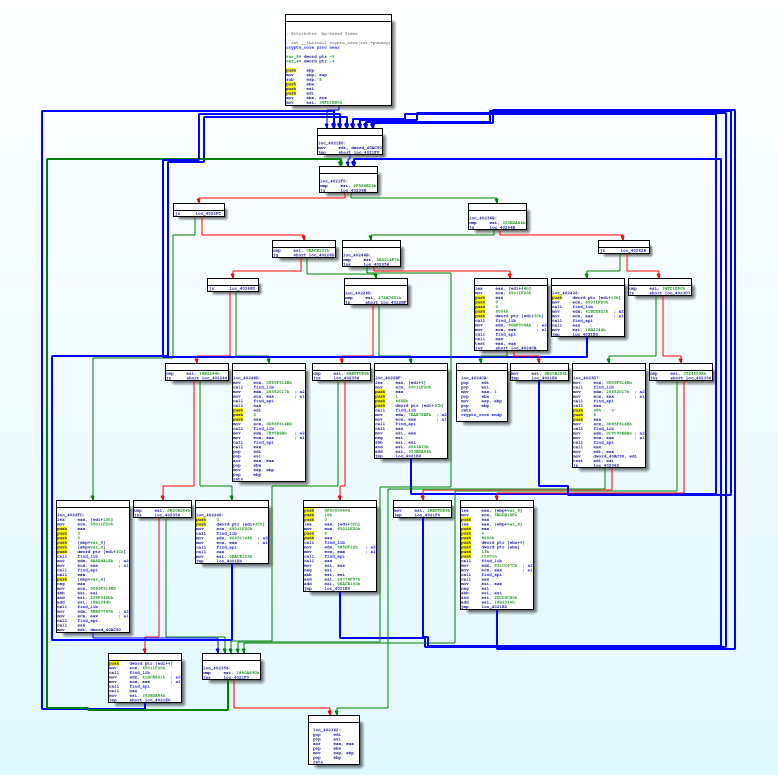
What’s up, Emotet? Emotet is one of the most widespread and havoc-wreaking malware families currently out there. Due to its modular structure, it’s able to easily evolve over time and gain new features without having to modify the core. Its first version dates back to 2014. Back then …
Read more -
Free decryption tool for Mapo ransomware
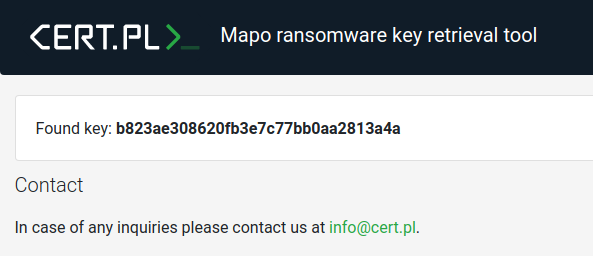
We are happy to announce that we are releasing a free decryption tool for the Mapo (a GarrantyDecrypt/Outsider variant) ransomware today. We would also like to thank Maciej Kotowicz of Kaspersky’s GReAT for sharing his insights on the ransomware’s encryption process. Our tool works with encrypted files …
Read more -
Brushaloader gaining new layers like a pro
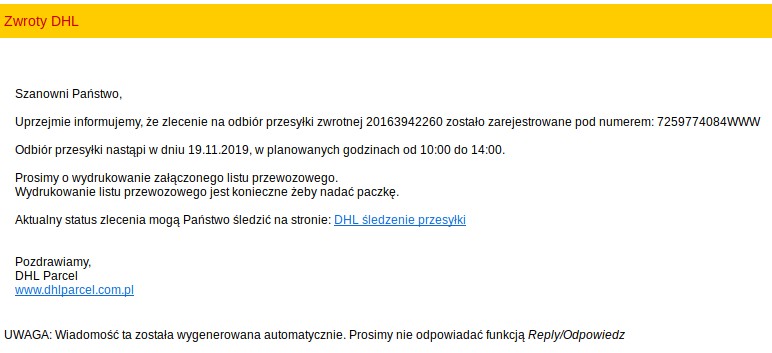
Yo dawg, I heard you like droppers so I put a dropper in your dropper On 2019-11-18 we received a report that some of Polish users have began receiving malspam imitating DHL: In this short article, we’ll take a look at the xls document that has been used as …
Read more -
Strengthening our malware analysis capabilities

During last year we have collaborated with Hatching.io on improving the open source Cuckoo Sandbox. The main works were focused on porting advanced mechanisms for memory analysis which were developed internally by our team in the previous years. The public release of the onemon marks the last stage of …
Read more -
Detricking TrickBot Loader
TrickBot (TrickLoader) is a modular financial malware that first surfaced in October in 20161. Almost immediately researchers have noticed similarities with a credential-stealer called Dyre. It is still believed that those two families might’ve been developed by the same actor. But in this article we will not focus …
Read more -
MWDB – our way to share information about malicious software
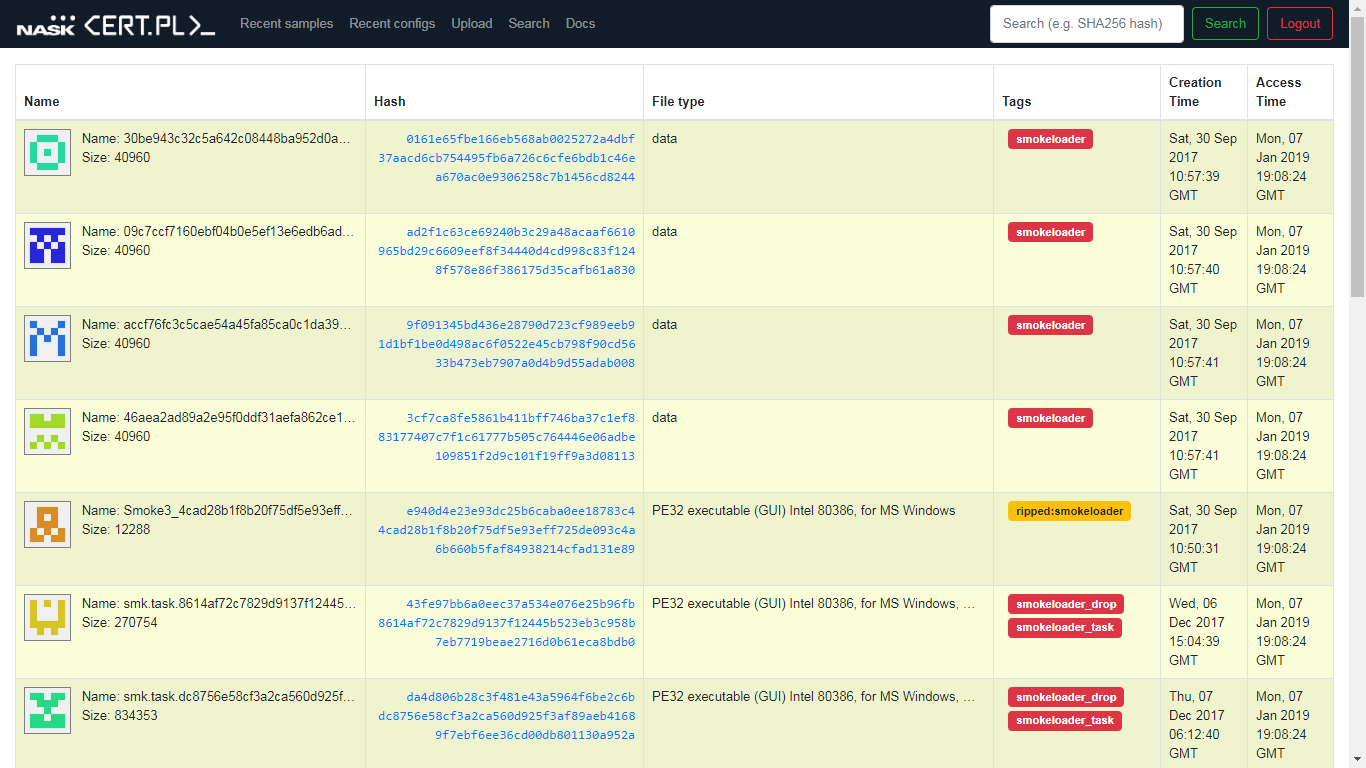
Analysis of current threats is one of the most common challenges facing almost any organization dealing with cybersecurity. From year to year, it also becomes a harder nut to crack, being undoubtedly influenced by the growing scale of activities undertaken by criminals and the degree of their advancement. In the …
Read more -
Dissecting Smoke Loader

Smoke Loader (also known as Dofoil) is a relatively small, modular bot that is mainly used to drop various malware families. Even though it’s designed to drop other malware, it has some pretty hefty malware-like capabilities on its own. Despite being quite old, it’s still going strong, recently …
Read more